Practice Free D-CSF-SC-23 Exam Online Questions
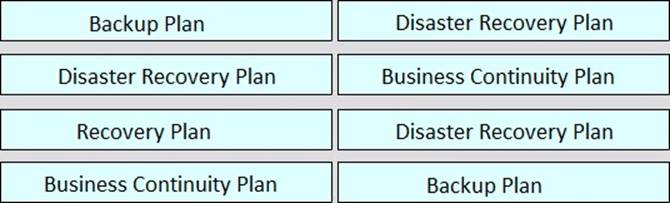
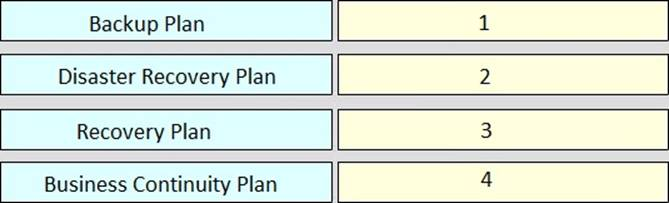
Rank order the relative severity of impact to an organization of each plan, where “1” signifies the most impact and “4” signifies the least impact.
An organization has a policy to respond “ASAP” to security incidents. The security team is having a difficult time prioritizing events because they are responding to all of them, in order of receipt.
Which part of the IRP does the team need to implement or update?
- A . Scheduling of incident responses
- B . ‘Post mortem’ documentation
- C . Classification of incidents
- D . Containment of incidents
A company suffers a data breach and determines that the threat actors stole or compromised 10,000 user profiles. The company had planned for such a breach and determined the loss would be around $2 million. Soon after restoration, the company stock suffered a 30% drop and the loss was nearly $20 million. In addition, the company received negative press.
Which area of risk did the business forget to account for?
- A . Litigation or Legal Risk
- B . Reputational Risk
- C . Vulnerability risk
- D . Business Operational Risk
What should an organization use to effectively mitigate against password sharing to prevent unauthorized access to systems?
- A . Access through a ticketing system
- B . Frequent password resets
- C . Strong password requirements
- D . Two factor authentication
A new employee is starting work at your company. When should they be informed of the company’s security policy?
- A . Based on human resource policy
- B . After the first security infraction
- C . Annual security policy review
- D . During regular security awareness sessions
Which NIST Cybersecurity Framework component defines activities and references for a specific cybersecurity approach?
- A . Profile
- B . Core
- C . Category
- D . Tiers
A bank has been alerted to a breach of its reconciliation systems. The notification came from the cybercriminals claiming responsibility in an email to the CEO. The CEO has alerted the company CSIRT.
What does the Communication Plan for the IRP specifically guide against?
- A . Transfer of chain of custody
- B . Accelerated turn over
- C . Rushed disclosure
- D . Initiating kill chain
Unrecoverable assets are specifically addressed in which function?
- A . Identify
- B . Respond
- C . Protect
- D . Recover
A company failed to detect a breach of their production system. The breach originated from a legacy system that was originally thought to be decommissioned. It turned out that system was still operating and occasionally connected to the production system for reporting purposes.
Which part of the process failed?
- A . DE.CM
- B . ID.BE
- C . ID.AM
- D . PR.DS
What activity informs situational awareness of the security status of an organization’s systems?
- A . IDP
- B . RMF
- C . ISCM
- D . DPI