Practice Free D-CSF-SC-01 Exam Online Questions
What contains a predefined set of instructions or processes that describes the management policy, procedures, and written plan defining recovery of information systems?
- A . RAS
- B . DRP
- C . BIA
- D . BCP
The ___ function within the framework emphasizes the identification of cybersecurity events in a timely manner.
- A . Identify
- B . Detect
- C . Respond
- D . Recover
A security engineer is responsible for monitoring company software, firmware, system OS, and applications for known vulnerabilities.
How should they stay current on exploits and information security?
- A . Implement security awareness training
- B . Update company policies and procedures
- C . Revise vulnerability management plan
- D . Subscribe to security mailing lists
Concerning a risk management strategy, what should the executive level be responsible for communicating?
- A . Risk mitigation
- B . Risk profile
- C . Risk tolerance
- D . Asset risk
To generate an accurate risk assessment, organizations need to gather information in what areas?
- A . Assets, Threats, Vulnerabilities, and Impact
- B . Assets, Vulnerabilities, Security, and Response
- C . Inventory, Security, Response, and Impact
- D . Inventory, Threats, Security, and Impact
A healthcare organization implements strong access controls to restrict access to patient data only to authorized personnel.
Which Protect Function subcategory is this organization focusing on?
- A . Data Security
- B . Access Control
- C . Protective Technology
- D . Baseline Configuration
Refer to the exhibit.
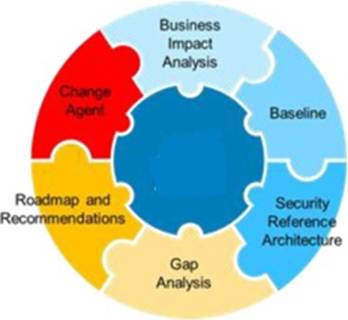
What is shown?
- A . ILM
- B . SDLC
- C . CSF
- D . CRLC
What corporate strategy is used to guide efforts after a catastrophic event and is implemented to ensure the return to normal business activity?
- A . Disaster Recovery Plan
- B . Continuity of Operations Plan
- C . Contingency Plan
- D . Business Continuity Plan
What activity informs situational awareness of the security status of an organization’s systems?
- A . IDP
- B . RMF
- C . ISCM
- D . DPI
A financial institution has deployed Intrusion Detection Systems (IDS) to monitor network traffic for unusual activity.
This aligns with which Detect Function subcategory?
- A . Detection Processes
- B . Risk Assessment
- C . Continuous Monitoring
- D . Asset Management
