Practice Free D-CI-DS-23 Exam Online Questions
Uses hypervisor to create a VM snapshot
A) Agent-based backup
B) Image-based backup
C) Changed Block Tracking
D) Continuous Data Protection
- A . 1-B, 2-A, 3-C, 4-D
- B . 1-B, 2-C, 3-D, 4-A
- C . 1-A, 2-D, 3-C, 4-B
- D . 1-C, 2-A, 3-D, 4-B
Refer to the exhibit.
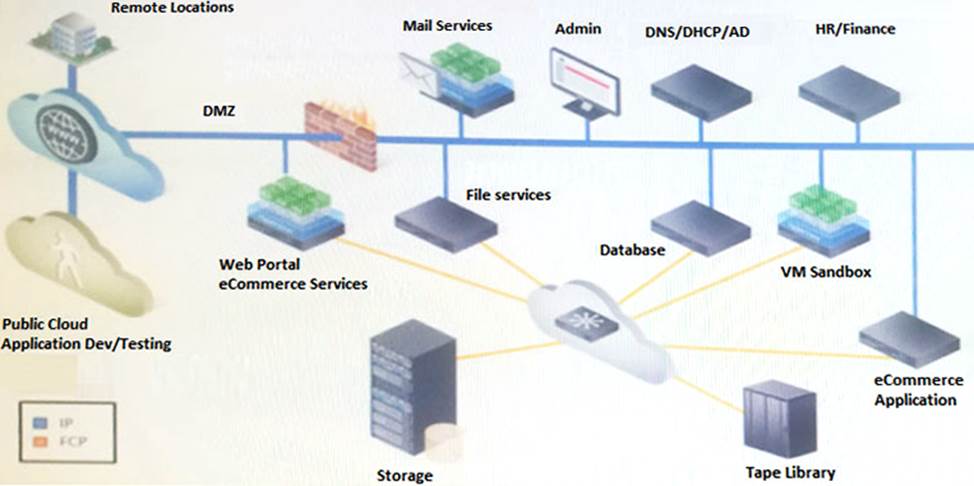
Your company recently negotiated several contracts with new customers to use its proprietary eCommerce system. As a result, the customer base has grown rapidly, which has introduced several challenges and requirements.
Business requirements:
– Applications need to scale quickly
– Metrics and reporting to anticipate business trends and efficient use of resources
– External customers are looking to license the eCommerce application
Other considerations:
– Applications need to be recorded for the public cloud
– Address security vulnerabilities for customer data in the cloud
Refer to Case 1.
You are tasked with designing a cloud. You review the existing infrastructure and business requirements. You select a CI solution to replace the existing Platform 2.0 infrastructure.
Before presenting this solution to the company, you must calculate the 3-year TCO using the following criteria:
Hardware maintenance = $ 35,000
Software maintenance = $ 20,000
Storage = $ 2,000 (2TB @ $ 1/GB)
What is the correct TCO value?
- A . $ 57,000
- B . $ 61,000
- C . $ 171,000
- D . $ 183,000
Which benefits might be realized by designing a separate infrastructure pool to host network functions?
- A . Reduced public IP address consumption, reduced troubleshooting time, and reduced consumer in frastructure load
- B . Reduced troubleshooting time, reduced consumer infrastructure load, and enhanced security
- C . Reduced troubleshooting time, enhanced security, and reduced public IP address consumption
- D . Reduced consumer infrastructure load, enhanced security, and reduced public IP address consumption
When designing a disaster recovery strategy, what is a common objective regarding Recovery Time Objective (RTO)?
- A . To minimize downtime at any cost
- B . To maximize data loss during a disaster
- C . To meet business-defined recovery time goals
- D . To ignore the importance of data recovery
An organization is considering the use of a cloud gateway to back up services in their private cloud environment. They want to use their existing backup application.
What should they ensure about the cloud gateway appliance?
- A . Supported by the backup application
Supports the target object storage APIs - B . Supported by the hypervisor
Supports the target object storage APIs - C . Supported by the backup application
Supports the target SMB storage APIs - D . Supported by the hypervisor
Supports the target SMB storage APIs
If the metering tool supports multi-tenancy and integrates with the cloud portal, what should be considered?
- A . Only permit local user access for security reasons
- B . Metering tool should not integrate with tenant authentication
- C . Metering server access should be allowed for all tenants
- D . Role-based access for security reasons
During the assessment phase of the design process, the cloud architect discovers that an organization wants to provide consumers with the ability to backup and restore entire virtual machines.
Which backup application functionality will support this requirement?
- A . Agent-based backups
- B . Image-based backups
- C . Array-based snapshots
- D . Cloud gateway backups
What accurately describes a method for delivering consumable resources using standards, policies, software, and protocols that enable provisioning, control, and configuration through a programmable interface?
- A . Hyper-converged
- B . Software-defined
- C . DevOps
- D . Converged
A cloud architect is evaluating an organization’s need for encryption.
Which type of encryption allows the deletion of data on disk by simply deleting the encryption key?
- A . Embedded
- B . Application
- C . File
- D . File system
What distinguishes cloud monitoring systems from their traditional IT counterparts?
- A . Provides telemetry to support orchestration
- B . Expects applications to monitor themselves
- C . Supports elasticity by consuming cloud resources natively
- D . Collects more data points than traditional monitoring
