Practice Free CS0-003 Exam Online Questions
A security analyst obtained the following table of results from a recent vulnerability assessment that was conducted against a single web server in the environment:
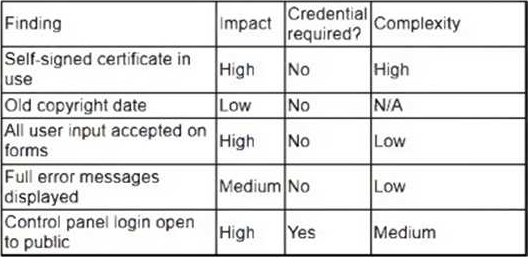
Which of the following should be completed first to remediate the findings?
- A . Ask the web development team to update the page contents
- B . Add the IP address allow listing for control panel access
- C . Purchase an appropriate certificate from a trusted root CA
- D . Perform proper sanitization on all fields
The Chief Information Security Officer is directing a new program to reduce attack surface risks and threats as part of a zero trust approach. The IT security team is required to come up with priorities for the program.
Which of the following is the best priority based on common attack frameworks?
- A . Reduce the administrator and privileged access accounts
- B . Employ a network-based IDS
- C . Conduct thorough incident response
- D . Enable SSO to enterprise applications
During an incident response procedure, a security analyst acquired the needed evidence from the hard drive of a compromised machine.
Which of the following actions should the analyst perform next to ensure the data integrity of the evidence?
- A . Generate hashes for each file from the hard drive.
- B . Create a chain of custody document.
- C . Determine a timeline of events using correct time synchronization.
- D . Keep the cloned hard drive in a safe place.
The security operations team is required to consolidate several threat intelligence feeds due to redundant tools and portals.
Which of the following will best achieve the goal and maximize results?
- A . Single pane of glass
- B . Single sign-on
- C . Data enrichment
- D . Deduplication
Legacy medical equipment, which contains sensitive data, cannot be patched.
Which of the following is the best solution to improve the equipment’s security posture?
- A . Move the legacy systems behind a WAR
- B . Implement an air gap for the legacy systems.
- C . Place the legacy systems in the perimeter network.
- D . Implement a VPN between the legacy systems and the local network.
A security analyst is investigating a compromised Linux server.
The analyst issues the ps command and receives the following output:

Which of the following commands should the administrator run next to further analyze the compromised system?
- A . gbd /proc/1301
- B . rpm -V openssh-server
- C . /bin/Is -1 /proc/1301/exe
- D . kill -9 1301
A malicious actor has gained access to an internal network by means of social engineering. The actor does not want to lose access in order to continue the attack.
Which of the following best describes the current stage of the Cyber Kill Chain that the threat actor is currently operating in?
- A . Weaponization
- B . Reconnaissance
- C . Delivery
- D . Exploitation
A company is implementing a vulnerability management program and moving from an on-premises environment to a hybrid IaaS cloud environment.
Which of the following implications should be considered on the new hybrid environment?
- A . The current scanners should be migrated to the cloud
- B . Cloud-specific misconfigurations may not be detected by the current scanners
- C . Existing vulnerability scanners cannot scan laaS systems
- D . Vulnerability scans on cloud environments should be performed from the cloud
A security alert was triggered when an end user tried to access a website that is not allowed per organizational policy. Since the action is considered a terminable offense, the SOC analyst collects the authentication logs, web logs, and temporary files, reflecting the web searches from the user’s workstation, to build the case for the investigation.
Which of the following is the best way to ensure that the investigation complies with HR or privacy policies?
- A . Create a timeline of events detailinq the date stamps, user account hostname and IP information associated with the activities
- B . Ensure that the case details do not reflect any user-identifiable information Password protect the evidence and restrict access to personnel related to the investigation
- C . Create a code name for the investigation in the ticketing system so that all personnel with access will not be able to easily identity the case as an HR-related investigation
- D . Notify the SOC manager for awareness after confirmation that the activity was intentional
A security analyst notices the following proxy log entries:

Which of the following is the user attempting to do based on the log entries?
- A . Use a DoS attack on external hosts.
- B . Exfiltrate data.
- C . Scan the network.
- D . Relay email.
