Practice Free CS0-003 Exam Online Questions
The security team reviews a web server for XSS and runs the following Nmap scan:

Which of the following most accurately describes the result of the scan?
- A . An output of characters > and " as the parameters used m the attempt
- B . The vulnerable parameter ID hccp://l72.31.15.2/1.php?id-2 and unfiltered characters returned
- C . The vulnerable parameter and unfiltered or encoded characters passed > and " as unsafe
- D . The vulnerable parameter and characters > and " with a reflected XSS attempt
An organization wants to move non-essential services into a cloud computing environment. The management team has a cost focus and would like to achieve a recovery time objective of 12 hours.
Which of the following cloud recovery strategies would work best to attain the desired outcome?
- A . Duplicate all services in another instance and load balance between the instances.
- B . Establish a hot site with active replication to another region within the same cloud provider.
- C . Set up a warm disaster recovery site with the same cloud provider in a different region.
- D . Configure the systems with a cold site at another cloud provider that can be used for failover.
An organization conducted a web application vulnerability assessment against the corporate website, and the following output was observed:
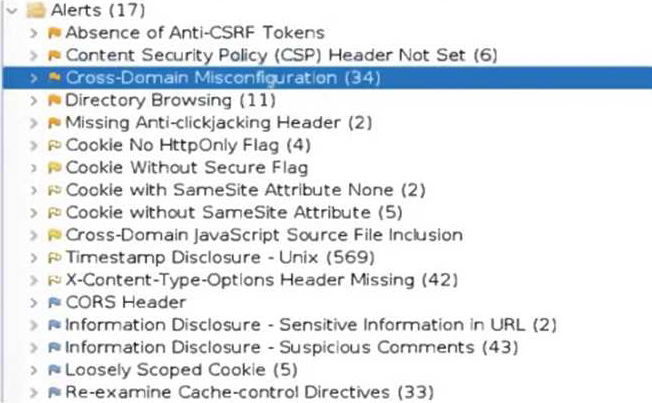
Which of the following tuning recommendations should the security analyst share?
- A . Set an HttpOnlvflaq to force communication by HTTPS
- B . Block requests without an X-Frame-Options header
- C . Configure an Access-Control-Allow-Origin header to authorized domains
- D . Disable the cross-origin resource sharing header
A security analyst who works in the SOC receives a new requirement to monitor for indicators of
compromise.
Which of the following is the first action the analyst should take in this situation?
- A . Develop a dashboard to track the indicators of compromise.
- B . Develop a query to search for the indicators of compromise.
- C . Develop a new signature to alert on the indicators of compromise.
- D . Develop a new signature to block the indicators of compromise.
A technician working at company.com received the following email:

After looking at the above communication, which of the following should the technician recommend to the security team to prevent exposure of sensitive information and reduce the risk of corporate data being stored on non-corporate assets?
- A . Forwarding of corporate email should be disallowed by the company.
- B . A VPN should be used to allow technicians to troubleshoot computer issues securely.
- C . An email banner should be implemented to identify emails coming from external sources.
- D . A rule should be placed on the DLP to flag employee IDs and serial numbers.
The following output is from a tcpdump al the edge of the corporate network:
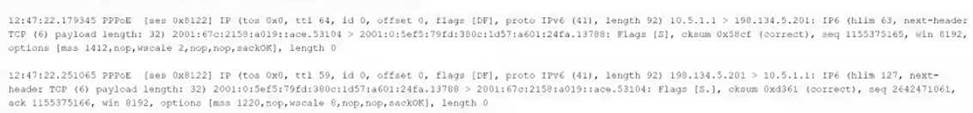
Which of the following best describes the potential security concern?
- A . Payload lengths may be used to overflow buffers enabling code execution.
- B . Encapsulated traffic may evade security monitoring and defenses
- C . This traffic exhibits a reconnaissance technique to create network footprints.
- D . The content of the traffic payload may permit VLAN hopping.
A security analyst received a malicious binary file to analyze.
Which of the following is the best technique to perform the analysis?
- A . Code analysis
- B . Static analysis
- C . Reverse engineering
- D . Fuzzing
An older CVE with a vulnerability score of 7.1 was elevated to a score of 9.8 due to a widely available exploit being used to deliver ransomware.
Which of the following factors would an analyst most likely communicate as the reason for this escalation?
- A . Scope
- B . Weaponization
- C . CVSS
- D . Asset value
Which of the following phases of the Cyber Kill Chain involves the adversary attempting to establish communication with a successfully exploited target?
- A . Command and control
- B . Actions on objectives
- C . Exploitation
- D . Delivery
A security analyst obtained the following table of results from a recent vulnerability assessment that was conducted against a single web server in the environment:
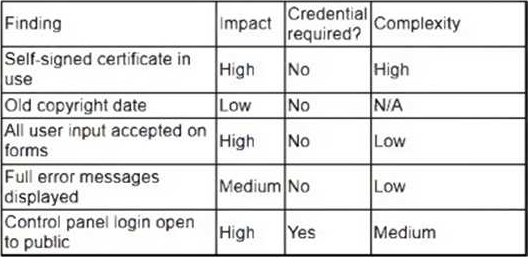
Which of the following should be completed first to remediate the findings?
- A . Ask the web development team to update the page contents
- B . Add the IP address allow listing for control panel access
- C . Purchase an appropriate certificate from a trusted root CA
- D . Perform proper sanitization on all fields
