Practice Free CAS-004 Exam Online Questions
An IT director is working on a solution to meet the challenge of remotely managing laptop devices and securely locking them down.
The solution must meet the following requirements:
• Cut down on patch management.
• Make use of standard configurations.
• Allow for custom resource configurations.
• Provide access to the enterprise system from multiple types of devices.
Which of the following would meet these requirements?
- A . MDM
- B . Emulator
- C . Hosted hypervisor
- D . VDI
D
Explanation:
A Virtual Desktop Infrastructure (VDI) solution meets all the listed requirements: reducing patch management, using standard configurations, allowing for custom resource configurations, and providing access from multiple device types. VDI allows centralized management of desktop environments, where patches and updates can be applied once and distributed across all virtual desktops. It also supports flexible resource configurations and secure remote access from various devices. CASP+ highlights VDI as a solution for centralized, secure desktop management that meets modern enterprise needs for mobility and security.
Reference: CASP+ CAS-004 Exam Objectives: Domain 3.0 C Enterprise Security Architecture (VDI for Secure Remote Desktop Management)
CompTIA CASP+ Study Guide: Virtual Desktop Infrastructure for Centralized Management and Security
A security analyst receives an alert from the SIEM regarding unusual activity on an authorized public SSH jump server. To further investigate, the analyst pulls the event logs directly from /var/log/auth.log: graphic.ssh_auth_log.
Which of the following actions would BEST address the potential risks by the activity in the logs?
- A . Alerting the misconfigured service account password
- B . Modifying the AllowUsers configuration directive
- C . Restricting external port 22 access
- D . Implementing host-key preferences
B
Explanation:
Reference: https://www.rapid7.com/blog/post/2017/10/04/how-to-secure-ssh-server-using-port-knocking-on-ubuntu-linux/
The AllowUsers configuration directive is an option for SSH servers that specifies which users are allowed to log in using SSH. The directive can include usernames, hostnames, IP addresses, or patterns. The directive can also be negated with a preceding exclamation mark (!) to deny access to specific users.
The logs show that there are multiple failed login attempts from different IP addresses using different usernames, such as root, admin, test, etc. This indicates a brute-force attack that is trying to guess the SSH credentials. To address this risk, the security analyst should modify the AllowUsers configuration directive to only allow specific users or hosts that are authorized to access the SSH jump server. This will prevent unauthorized users from attempting to log in using SSH and reduce the attack surface.
Reference:
https://man.openbsd.org/sshd_config#AllowUsers
https://www.ssh.com/academy/ssh/brute-force
A security analyst receives an alert from the SIEM regarding unusual activity on an authorized public SSH jump server. To further investigate, the analyst pulls the event logs directly from /var/log/auth.log: graphic.ssh_auth_log.
Which of the following actions would BEST address the potential risks by the activity in the logs?
- A . Alerting the misconfigured service account password
- B . Modifying the AllowUsers configuration directive
- C . Restricting external port 22 access
- D . Implementing host-key preferences
B
Explanation:
Reference: https://www.rapid7.com/blog/post/2017/10/04/how-to-secure-ssh-server-using-port-knocking-on-ubuntu-linux/
The AllowUsers configuration directive is an option for SSH servers that specifies which users are allowed to log in using SSH. The directive can include usernames, hostnames, IP addresses, or patterns. The directive can also be negated with a preceding exclamation mark (!) to deny access to specific users.
The logs show that there are multiple failed login attempts from different IP addresses using different usernames, such as root, admin, test, etc. This indicates a brute-force attack that is trying to guess the SSH credentials. To address this risk, the security analyst should modify the AllowUsers configuration directive to only allow specific users or hosts that are authorized to access the SSH jump server. This will prevent unauthorized users from attempting to log in using SSH and reduce the attack surface.
Reference:
https://man.openbsd.org/sshd_config#AllowUsers
https://www.ssh.com/academy/ssh/brute-force
Application owners are reporting performance issues with traffic using port 1433 from the cloud environment. A security administrator has various pcap files to analyze the data between the related source and destination servers.
Which of the following tools should be used to help troubleshoot the issue?
- A . Fuzz testing
- B . Wireless vulnerability scan
- C . Exploit framework
- D . Password cracker
- E . Protocol analyzer
E
Explanation:
A protocol analyzer, such as Wireshark, is a tool used to capture and analyze network traffic. It allows security administrators to inspect individual packets, understand the traffic flow, and identify any unusual patterns or issues that may be impacting performance, such as high latency or unusual volume of traffic on a specific port.
A company wants to improve the security of its web applications that are running on in-house servers A risk assessment has been performed and the following capabilities are desired:
• Terminate SSL connections at a central location
• Manage both authentication and authorization for incoming and outgoing web service calls
• Advertise the web service API
• Implement DLP and anti-malware features
Which of the following technologies will be the BEST option?
- A . WAF
- B . XML gateway
- C . ESB gateway
- D . API gateway
D
Explanation:
An API gateway is a device or software that acts as an intermediary between clients and servers that provide web services through application programming interfaces (APIs).
An API gateway can provide various functions such as:
Terminating SSL connections at a central location, reducing the overhead on the backend servers and simplifying certificate management
Managing both authentication and authorization for incoming and outgoing web service calls, enforcing security policies and access control
Advertising the web service API, providing documentation and discovery features for developers and
consumers
Implementing DLP and anti-malware features, preventing data leakage and malicious code injection A web application firewall (WAF) is a device or software that filters and blocks malicious web traffic from reaching an application. A WAF can provide some protection for web services, but it does not provide all the functions of an API gateway. An XML gateway is a device or software that validates, transforms, and routes XML messages between clients and servers that provide web services. An XML gateway can provide some functions of an API gateway, but it is limited to XML-based web services and does not support other formats such as JSON. An enterprise service bus (ESB) gateway is a device or software that integrates and orchestrates multiple web services into a single service or application. An ESB gateway can provide some functions of an API gateway, but it is more focused on business logic and workflow rather than security and performance.
Reference: [CompTIA Advanced Security Practitioner (CASP+) Certification Exam Objectives], Domain 2: Enterprise Security Architecture, Objective 2.3: Implement solutions for the secure use of cloud services
In order to authenticate employees who, call in remotely, a company’s help desk staff must be able to view partial Information about employees because the full information may be considered sensitive.
Which of the following solutions should be implemented to authenticate employees?
- A . Data scrubbing
- B . Field masking
- C . Encryption in transit
- D . Metadata
B
Explanation:
Field masking is a technique that hides or obscures part of the information in a data field, such as a password, credit card number, or social security number. Field masking can be used to protect sensitive or confidential data from unauthorized access or disclosure, while still allowing authorized users to view or verify the data.
Field masking should be implemented to authenticate employees who call in remotely by allowing the help desk staff to view partial information about employees, because field masking would: Enable the help desk staff to verify the identity of the employees by asking them to provide some characters or digits from their data fields, such as their employee ID or email address.
Prevent the help desk staff from viewing the full information about employees, which may be considered sensitive and subject to privacy regulations or policies.
Reduce the risk of data leakage, theft, or misuse by limiting the exposure of sensitive data to only those who need it.
A customer reports being unable to connect to a website at www.test.com to consume services.
The customer notices the web application has the following published cipher suite:
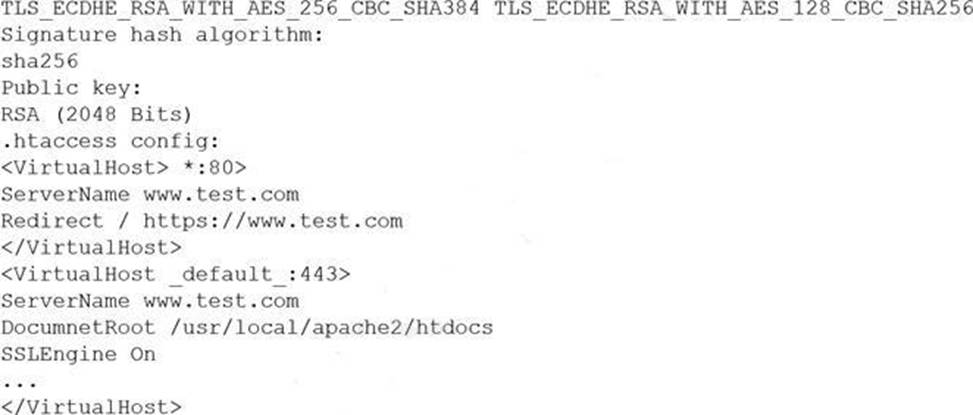
Which of the following is the MOST likely cause of the customer’s inability to connect?
- A . Weak ciphers are being used.
- B . The public key should be using ECDSA.
- C . The default should be on port 80.
- D . The server name should be test.com.
A
Explanation:
Reference: https://security.stackexchange.com/questions/23383/ssh-key-type-rsa-dsa-ecdsa-are-there-easy-answers-for-which-to-choose-when
A security analyst runs a vulnerability scan on a network administrator’s workstation The network administrator has direct administrative access to the company’s SSO web portal The vulnerability scan uncovers cntical vulnerabilities with equally high CVSS scores for the user’s browser, OS, email client and an offline password manager.
Which of the following should the security analyst patch FIRST?
- A . Email client
- B . Password manager
- C . Browser
- D . OS
C
Explanation:
The browser is the application that the security analyst should patch first, given that all the applications have equally high CVSS scores. CVSS stands for Common Vulnerability Scoring System, which is a method for measuring the severity of vulnerabilities based on various factors, such as access conditions, impact, and exploitability. CVSS scores range from 0 to 10, with higher scores indicating higher severity. However, CVSS scores alone are not sufficient to determine the patching priority, as they do not account for other factors, such as the likelihood of exploitation, the exposure of the system, or the criticality of the data. Therefore, the security analyst should also consider the context and the risk of each application when deciding which one to patch first. In this case, the browser is likely to be the most exposed and frequently used application by the network administrator, and also the most likely entry point for an attacker to compromise the system or access the SSO web portal. Therefore, patching the browser first can reduce the risk of a successful attack and protect the system and the data from further damage.
Verified Reference:
https://nvd.nist.gov/vuln-metrics/cvss
https://www.darkreading.com/risk/vulnerability-severity-scores-make-for-poor-patching-priority-researchers-find
A company has a BYOD policy and has configured remote-wiping capabilities to support security requirements. An executive has raised concerns about personal contacts and photos being deleted from personal devices when an employee is terminated.
Which of the following is the best way to address these concerns?
- A . Enforce the use of the approved email client.
- B . Require full device encryption.
- C . Disable geotagging on the devices.
- D . Implement containerization.
D
Explanation:
Containerization separates corporate data from personal data on BYOD devices. When an employee is terminated, only the corporate container is wiped, preserving personal data. This aligns with CASP+ objective 2.4, which emphasizes securing endpoint devices while respecting privacy.
An organization recently recovered from an attack that featured an adversary injecting Malicious logic into OS bootloaders on endpoint devices Therefore, the organization decided to require the use of TPM for measured boot and attestation, monitoring each component from the IJEFI through the full loading of OS components. of the following TPM structures enables this storage functionality?
- A . Endorsement tickets
- B . Clock/counter structures
- C . Command tag structures with MAC schemes
- D . Platform configuration registers
D
Explanation:
TPMs provide the ability to store measurements of code and data that can be used to ensure that code and data remain unchanged over time. This is done through Platform Configuration Registers (PCRs), which are structures used to store measurements of code and data. The measurements are taken during the boot process and can be used to compare the state of the system at different times, which can be used to detect any changes to the system and verify that the system has not been tampered with.
