Practice Free CAS-004 Exam Online Questions
A Chief Information Security Officer is concerned about the condition of the code security being used for web applications. It is important to get the review right the first time, and the company is willing to use a tool that will allow developers to validate code as it is written.
Which of the following methods should the company use?
- A . SAST
- B . DAST
- C . Fuzz testing
- D . Intercepting proxy
A
Explanation:
Static Application Security Testing (SAST) is the best method for validating code as it is written. SAST analyzes the source code or binaries of an application for vulnerabilities before the code is executed, allowing developers to identify and fix security flaws early in the development process. This method integrates into the development environment and provides real-time feedback, which is critical for ensuring secure coding practices from the start. CASP+ highlights the importance of SAST in secure software development lifecycles (SDLCs) as a proactive measure to prevent security issues before the code is deployed.
Reference: CASP+ CAS-004 Exam Objectives: Domain 2.0 C Enterprise Security Operations (SAST for Secure Code Validation)
CompTIA CASP+ Study Guide: Secure Software Development and Static Code Analysis
A junior security researcher has identified a buffer overflow vulnerability leading to remote code execution in a former employer’s software. The security researcher asks for the manager’s advice on the vulnerability submission process.
Which of the following is the best advice the current manager can provide the security researcher?
- A . Collect proof that the exploit works in order to expedite the process.
- B . Publish proof-of-concept exploit code on a personal blog.
- C . Recommend legal consultation about the process.
- D . Visit a bug bounty website for the latest information.
C
Explanation:
When a security researcher identifies a vulnerability, especially one involving remote code execution, they must navigate a process that protects them legally and ethically. The best advice here is to consult with legal professionals to understand any liabilities, such as potential violations of non-disclosure agreements (NDAs) or intellectual property concerns. Legal consultation ensures that the researcher follows responsible disclosure practices and avoids legal repercussions, which aligns with CASP+ guidance on managing vulnerabilities and the responsible handling of sensitive security information. CompTIA CASP+ emphasizes the importance of adhering to legal and regulatory frameworks when reporting vulnerabilities, especially when dealing with former employers or clients.
Reference: CASP+ CAS-004 Exam Objectives: Domain 1.0 C Risk Management (Responsible Disclosure, Legal Concerns)
CompTIA CASP+ Study Guide: Handling Vulnerabilities and Legal Considerations
A major broadcasting company that requires continuous availability to streaming content needs to be resilient against DDoS attacks.
Which of the following is the MOST important infrastructure security design element to prevent an outage?
- A . Supporting heterogeneous architecture
- B . Leveraging content delivery network across multiple regions
- C . Ensuring cloud autoscaling is in place
- D . Scaling horizontally to handle increases in traffic
B
Explanation:
A content delivery network (CDN) is a distributed system of servers that delivers web content to users based on their geographic location, the origin of the content, and the performance of the network. A CDN can help improve the availability and performance of web applications by caching content closer to the users, reducing latency and bandwidth consumption. A CDN can also help mitigate distributed denial-of-service (DDoS) attacks by absorbing or filtering malicious traffic before it reaches the origin servers, reducing the impact on the application availability. Supporting heterogeneous architecture means using different types of hardware, software, or platforms in an IT environment. This can help improve resilience by reducing single points of failure and increasing compatibility, but it does not directly prevent DDoS attacks. Ensuring cloud autoscaling is in place means using cloud services that automatically adjust the amount of resources allocated to an application based on the demand or load. This can help improve scalability and performance by providing more resources when needed, but it does not directly prevent DDoS attacks. Scaling horizontally means adding more servers or nodes to an IT environment to increase its capacity or throughput. This can help improve scalability and performance by distributing the load across multiple servers, but it does not directly prevent DDoS attacks.
Reference: [CompTIA Advanced Security Practitioner (CASP+) Certification Exam Objectives], Domain 2: Enterprise Security Architecture, Objective 2.4: Select controls based on systems security evaluation models
A security architect is tasked with scoping a penetration test that will start next month. The architect wants to define what security controls will be impacted.
Which of the following would be the BEST document to consult?
- A . Rules of engagement
- B . Master service agreement
- C . Statement of work
- D . Target audience
C
Explanation:
The Statement of Work is a document that outlines the scope of the penetration test and defines the objectives, tools, methodology, and targets of the test. It also outlines the security controls that will be impacted by the test and what the expected outcomes are. Additionally, the Statement of Work should include any legal requirements and other considerations that should be taken into account during the penetration test.
Reference: CompTIA Advanced Security Practitioner (CASP+) Study Guide: Chapter 5: Security
Testing, Section 5.4: Defining Scope and Objective.
During a network defense engagement, a red team is able to edit the following registry key:
![]()
Which of the following tools is the red team using to perform this action?
- A . PowerShell
- B . SCAP scanner
- C . Network vulnerability scanner
- D . Fuzzer
A
Explanation:
PowerShell is a versatile scripting language that can be used to automate administrative tasks and configurations on Windows machines. It has the capability to edit registry keys, which is what the red team appears to have done based on the provided information. PowerShell is a common tool used by both system administrators and attackers (in the form of a red team during penetration testing).
A network administrator receives a ticket regarding an error from a remote worker who is trying to reboot a laptop. The laptop has not yet loaded the operating system, and the user is unable to continue the boot process. The administrator is able to provide the user with a recovery PIN, and the user is able to reboot the system and access the device as needed.
Which of the following is the MOST likely cause of the error?
- A . Lockout of privileged access account
- B . Duration of the BitLocker lockout period
- C . Failure of the Kerberos time drift sync
- D . Failure of TPM authentication
D
Explanation:
The most likely cause of the error is the failure of TPM authentication. TPM stands for Trusted Platform Module, which is a hardware component that stores encryption keys and other security information. TPM can be used by BitLocker to protect the encryption keys and verify the integrity of the boot process. If TPM fails to authenticate the laptop, BitLocker will enter recovery mode and ask for a recovery PIN, which is a 48-digit numerical password that can be used to unlock the system. The administrator should check the TPM status and configuration and make sure it is working properly.
Verified Reference:
https://support.microsoft.com/en-us/windows/finding-your-bitlocker-recovery-key-in-windows-6b71ad27-0b89-ea08-f143-056f5ab347d6
https://learn.microsoft.com/en-us/windows/security/operating-system-security/data-protection/bitlocker/bitlocker-recovery-guide-plan https://docs.sophos.com/esg/sgn/8-1/user/win/en-us/esg/SafeGuard-Enterprise/tasks/BitLockerRecoveryKey.html
A company security engineer arrives at work to face the following scenario:
1) Website defacement
2) Calls from the company president indicating the website needs to be fixed Immediately because It Is damaging the brand
3) A Job offer from the company’s competitor
4) A security analyst’s investigative report, based on logs from the past six months, describing how lateral movement across the network from various IP addresses originating from a foreign adversary country resulted in exfiltrated data
Which of the following threat actors Is MOST likely involved?
- A . Organized crime
- B . Script kiddie
- C . APT/nation-state
- D . Competitor
C
Explanation:
An Advanced Persistent Threat (APT) is an attack that is targeted, well-planned, and conducted over a long period of time by a nation-state actor. The evidence provided in the scenario indicates that the security analyst has identified a foreign adversary, which is strong evidence that an APT/nation-state actor is responsible for the attack.
Resources:
CompTIA Advanced Security Practitioner (CASP+) Study Guide, Chapter 5: “Advanced Persistent Threats,” Wiley, 2018. https://www.wiley.com/en-us/CompTIA+Advanced+Security+Practitioner+CASP%2B+Study+Guide%2C+2nd+Edition-p-9781119396582
A security architect is implementing a web application that uses a database back end. Prior to the production, the architect is concerned about the possibility of XSS attacks and wants to identify security controls that could be put in place to prevent these attacks.
Which of the following sources could the architect consult to address this security concern?
- A . SDLC
- B . OVAL
- C . IEEE
- D . OWASP
D
Explanation:
OWASP is a resource used to identify attack vectors and their mitigations, OVAL is a vulnerability assessment standard
OWASP (Open Web Application Security Project) is a source that the security architect could consult to address the security concern of XSS (cross-site scripting) attacks on a web application that uses a database back end. OWASP is a non-profit organization that provides resources and guidance for improving the security of web applications and services. OWASP publishes the OWASP Top 10 list of common web application vulnerabilities and risks, which includes XSS attacks, as well as recommendations and best practices for preventing or mitigating them. SDLC (software development life cycle) is not a source for addressing XSS attacks, but a framework for developing software in an organized and efficient manner. OVAL (Open Vulnerability and Assessment Language) is not a source for addressing XSS attacks, but a standard for expressing system configuration information and vulnerabilities. IEEE (Institute of Electrical and Electronics Engineers) is not a source for addressing XSS attacks, but an organization that develops standards for various fields of engineering and technology.
Verified Reference:
https://www.comptia.org/blog/what-is-owasp
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A security administrator has been tasked with hardening a domain controller against lateral movement attacks.
Below is an output of running services:
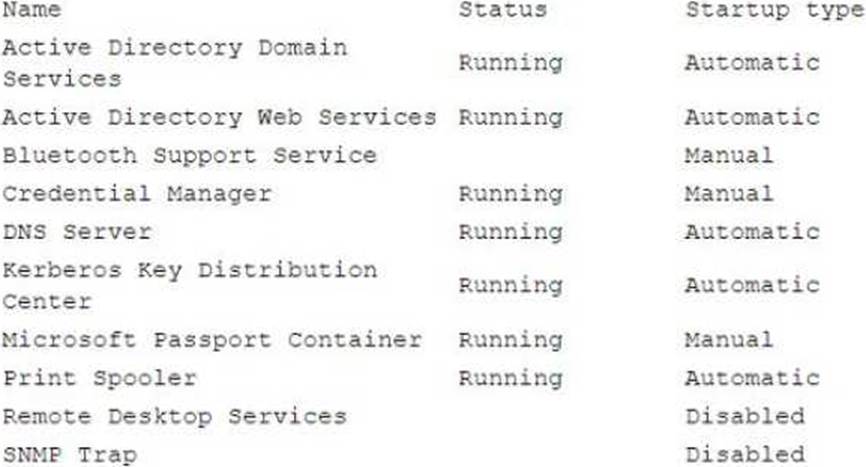
Which of the following configuration changes must be made to complete this task?
- A . Stop the Print Spooler service and set the startup type to disabled.
- B . Stop the DNS Server service and set the startup type to disabled.
- C . Stop the Active Directory Web Services service and set the startup type to disabled.
- D . Stop Credential Manager service and leave the startup type to disabled.
A
Explanation:
Stopping the Print Spooler service and setting the startup type to disabled is the best configuration change to harden a domain controller against lateral movement attacks. The Print Spooler service has been known to be vulnerable to remote code execution exploits that can allow attackers to gain access to domain controllers and other sensitive machines. Disabling this service can reduce the attack surface and prevent exploitation attempts.
A high-severity vulnerability was found on a web application and introduced to the enterprise. The vulnerability could allow an unauthorized user to utilize an open-source library to view privileged user information. The enterprise is unwilling to accept the risk, but the developers cannot fix the issue right away.
Which of the following should be implemented to reduce the risk to an acceptable level until the issue can be fixed?
- A . Scan the code with a static code analyzer, change privileged user passwords, and provide security training.
- B . Change privileged usernames, review the OS logs, and deploy hardware tokens.
- C . Implement MFA, review the application logs, and deploy a WAF.
- D . Deploy a VPN, configure an official open-source library repository, and perform a full application review for vulnerabilities.
C
Explanation:
Reference: https://www.microfocus.com/en-us/what-is/sast
Implementing MFA can add an extra layer of security to protect against unauthorized access if the vulnerability is exploited. Reviewing the application logs can help identify if any attempts have been made to exploit the vulnerability, and deploying a WAF can help block any attempts to exploit the vulnerability. While the other options may provide some level of security, they may not directly address the vulnerability and may not reduce the risk to an acceptable level.
