Practice Free CAS-004 Exam Online Questions
SIMULATION
You have received a report that some users are unable to use their personal devices to authenticate to a protected corporate website. The users have stated that no changes have been made on their personal devices since the last time they were able to authenticate successfully.
INSTRUCTIONS
Examine the device health policy for the MFA solution, the MFA usage logs, and the device telemetry. Using that information:
. Select the policy/policies that were violated.
. Select the telemetry log(s) that
explain(s) the policy violations.
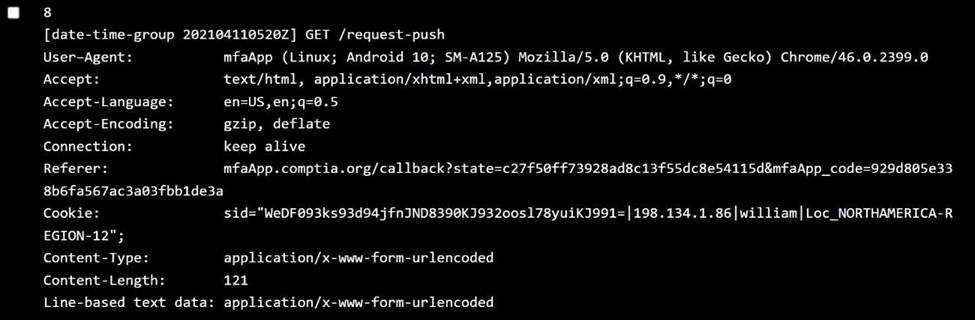
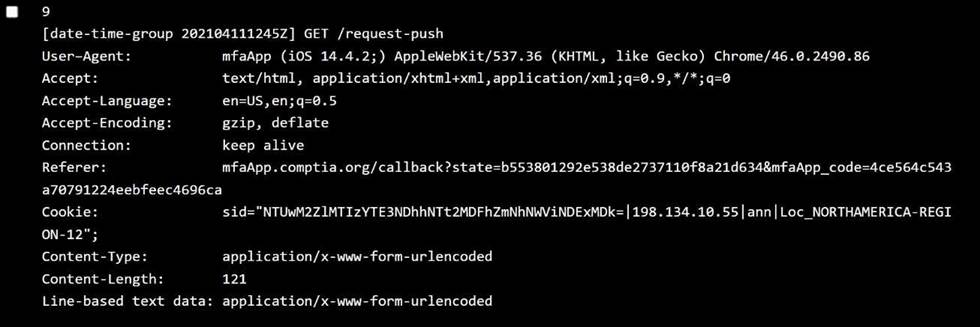
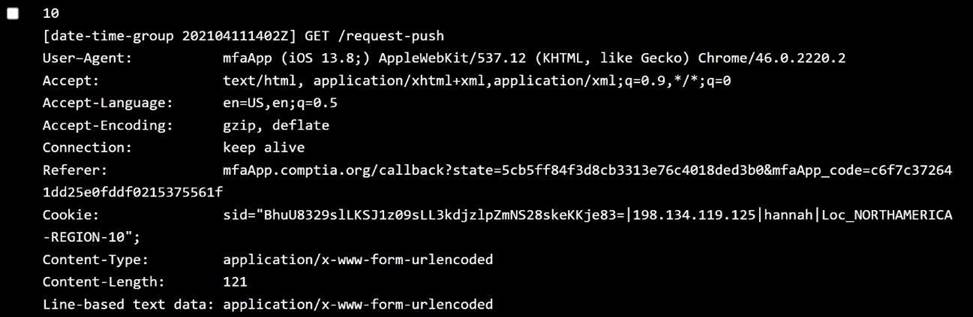
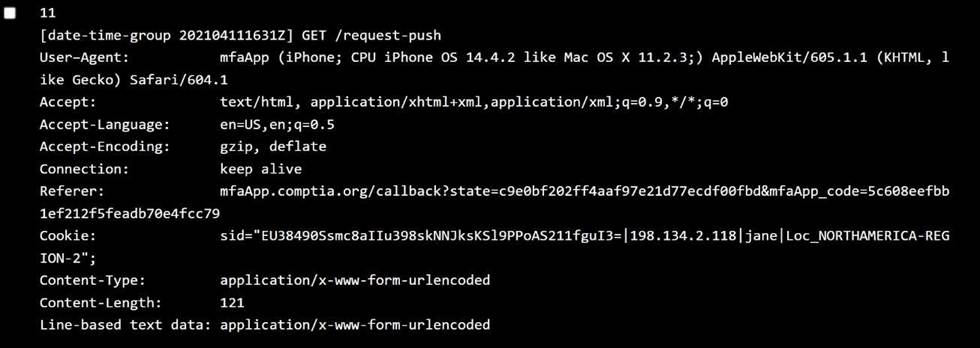
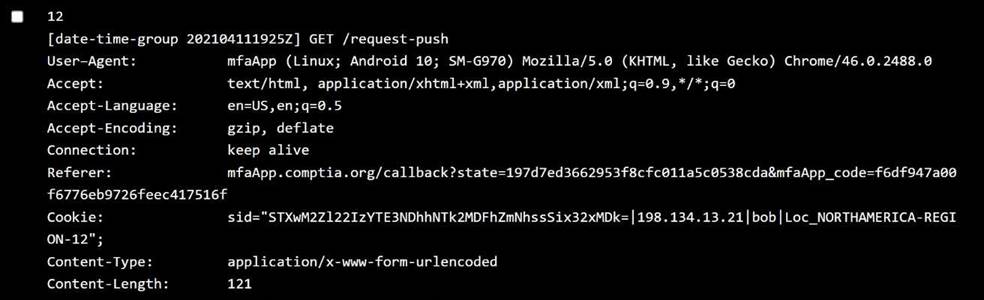
Issue: Userscannot authenticateusing personal devices. User claim: No changes have been made to their devices since they were last able to authenticate. Step 2: Review the Policy Settings
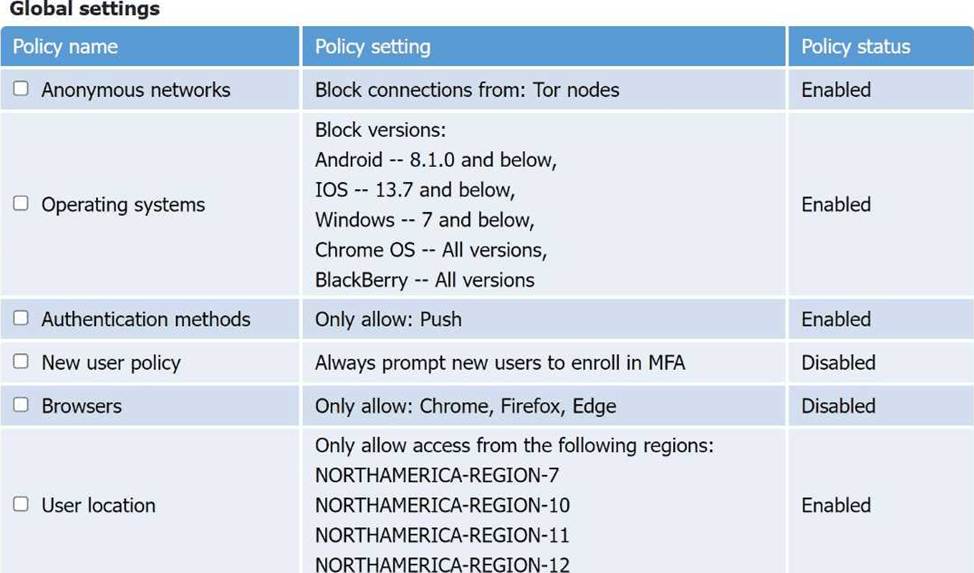
From theGlobal settingstable:
✅ Enabled Policies:
Anonymous networks: Blocks Tor ( ✅ )
Operating systems: Blocks:
Android 8.1.0 and below
iOS 13.7 and below
Windows 7 and below
Chrome OS (all)
BlackBerry (all)
Authentication method: Push only ( ✅ )
User location: Only allows regions:
NORTHAMERICA-REGION-7
NORTHAMERICA-REGION-10
NORTHAMERICA-REGION-11
NORTHAMERICA-REGION-12
Disabled Policies:
Browser restriction (Chrome, Firefox, Edge) is disabled (i.e., any browser is allowed)
New user policyisdisabled
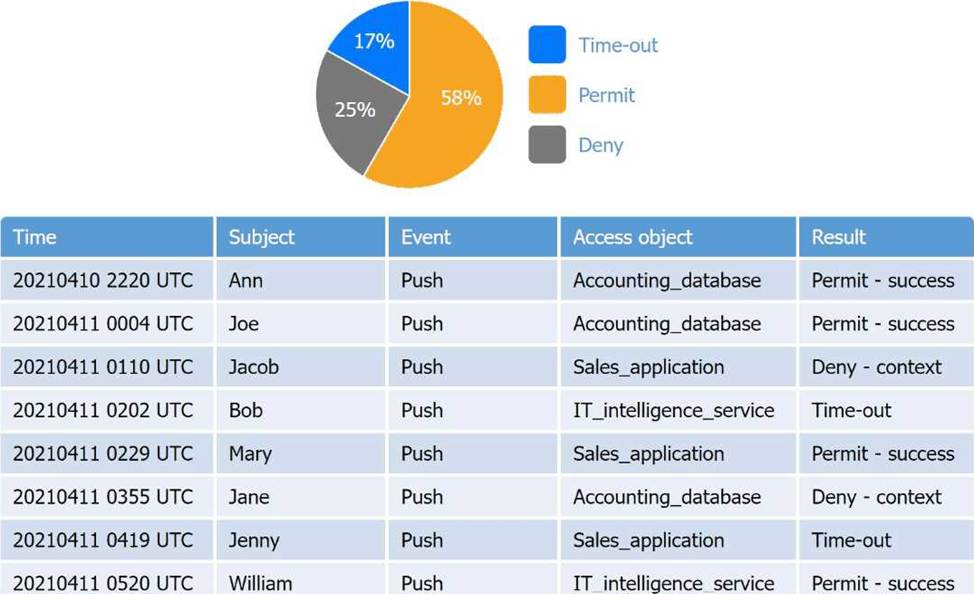
Step 3: Examine the Authentication Results Table
From the access log table:
Subject
Result
Access object
Jacob
Deny – context
Sales_application
Bob
Time-out
IT_intelligence_svc
Jane
Deny – context
Accounting_database
Jenny
Time-out
Sales_application
These four failed. Let’s match them with policies.
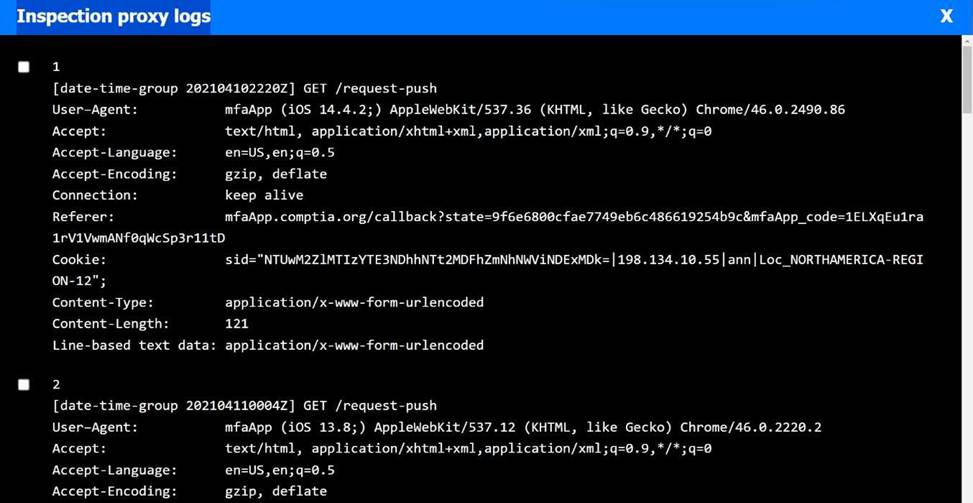
Step 4: Correlate With Telemetry Logs
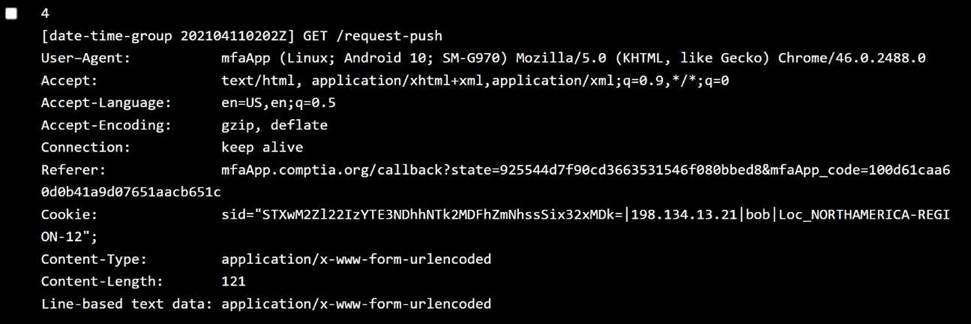
Jacob:
OS:iOS 13.0 →Below 13.7→ ❌ Violation ofOperating System policy Location:REGION not specified fully, assume okay unless proven otherwise ✅ Policy violated:Operating system
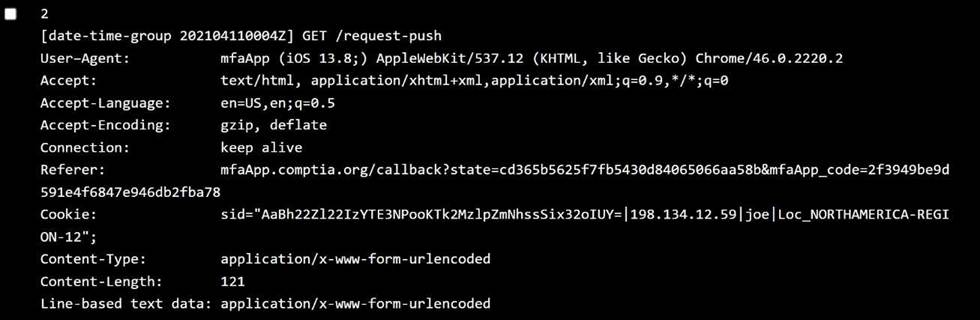
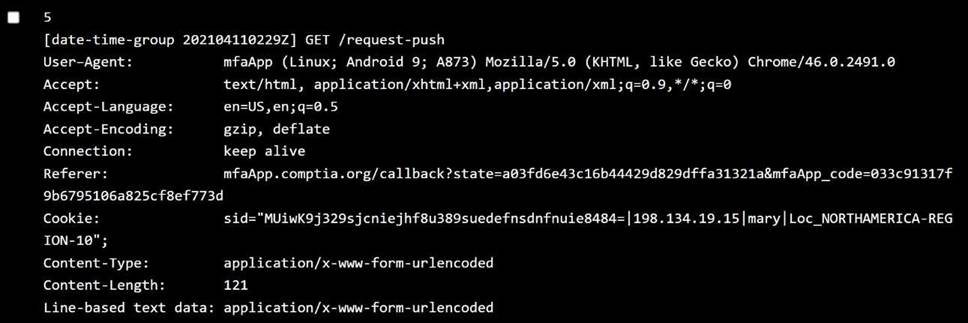
Bob:
OS:Android 10 → ✅ Allowed
Location:NORTHAMERICA-REGION-12 → ✅ Allowed Behavior:Time-outThis could be aconnectivityorpush timeout, not policy violation. ⛔️ Not due to policy violation
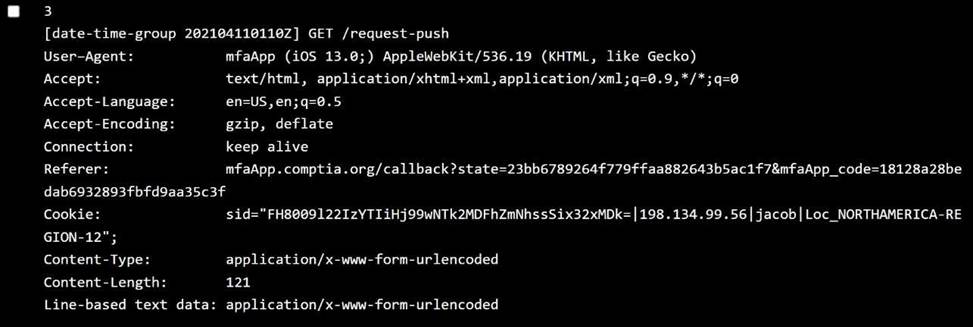
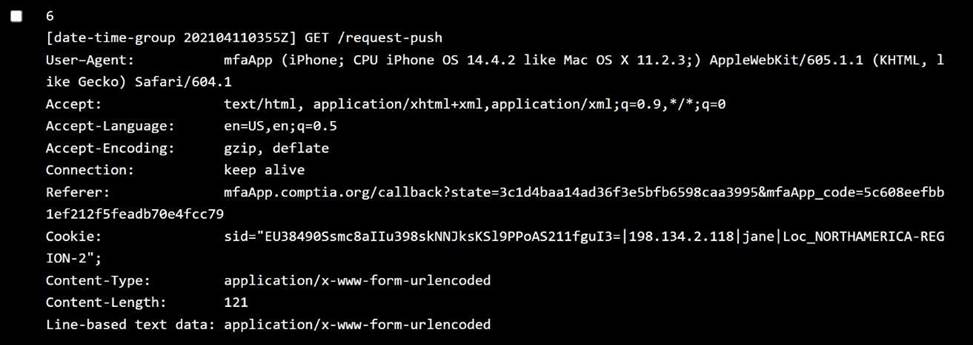
Jane:
OS:iOS 14.2 → ✅ Allowed
Location:NORTHAMERICA-REGION-6 → ❌ Not in allowed regions ✅ Policy violated:User location
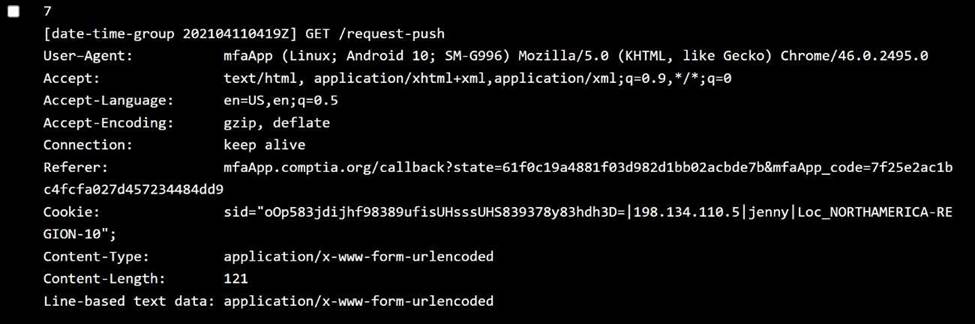
Jenny:
OS:Android 10 → ✅ Allowed
Location:NORTHAMERICA-REGION-6 → ❌ Not in allowed regions ✅ Policy violated:User location
✅ Step 5: Final Answer
Violated Policies:
✅ Operating Systems→ Violated byJacob
✅ User Location→ Violated byJaneandJenny
Telemetry Logs that explain violations:
Log 3C Jacob (OS iOS 13.0 → blocked)
Log 6C Jane (Region 6 → blocked)
Log 7C Jenny (Region 6 → blocked)
✔️ Final Answer Summary:
Policies Violated:
✅ Operating systems
✅ User location
Relevant Telemetry Logs:
Jacob → Log 3
Jane → Log 6
Jenny → Log 7
A network administrator for a completely air-gapped and closed system has noticed that anomalous external files have been uploaded to one of the critical servers. The administrator has reviewed logs in the SIEM that were collected from security appliances, network infrastructure devices, and endpoints.
Which of the following processes, if executed, would be MOST likely to expose an attacker?
- A . Reviewing video from IP cameras within the facility
- B . Reconfiguring the SIEM connectors to collect data from the perimeter network hosts
- C . Implementing integrity checks on endpoint computing devices
- D . Looking for privileged credential reuse on the network
A
Explanation:
Reviewing video from IP cameras within the facility would be the most likely process to expose an
attacker who has compromised an air-gapped system. Since air-gapped systems are isolated from
external networks, an attacker would need physical access to the system or use some covert channel
to communicate with it. Video surveillance could reveal any unauthorized or suspicious activity
within the facility that could be related to the attack.
Verified Reference:
https://www.welivesecurity.com/wp-content/uploads/2021/12/eset_jumping_the_air_gap_wp.pdf
https://en.wikipedia.org/wiki/Air-Gap_Malware
https://www.techtarget.com/searchsecurity/essentialguide/How-air-gap-attacks-challenge-the-notion-of-secure-networks
Which of the following security features do email signatures provide?
- A . Non-repudiation
- B . Body encryption
- C . Code signing
- D . Sender authentication
- E . Chain of custody
A
Explanation:
Email signatures provide non-repudiation, which ensures that the sender of an email cannot deny having sent it. A digital signature, when attached to an email, uses cryptographic techniques to verify the sender’s identity and confirm the authenticity of the message. This feature helps establish trust by preventing tampering and ensuring the integrity of the communication. CASP+ emphasizes the role of digital signatures in ensuring non-repudiation in secure communication protocols.
Reference: CASP+ CAS-004 Exam Objectives: Domain 2.0 C Enterprise Security Operations (Non-repudiation and Digital Signatures)
CompTIA CASP+ Study Guide: Email Security and Non-repudiation with Digital Signatures
A cybersecurity analyst receives a ticket that indicates a potential incident is occurring. There has been a large in log files generated by a generated by a website containing a ‘’Contact US’’ form. The analyst must determine if the increase in website traffic is due to a recent marketing campaign of if this is a potential incident.
Which of the following would BEST assist the analyst?
- A . Ensuring proper input validation is configured on the ‘’Contact US’’ form
- B . Deploy a WAF in front of the public website
- C . Checking for new rules from the inbound network IPS vendor
- D . Running the website log files through a log reduction and analysis tool
A systems administrator was given the following IOC to detect the presence of a malicious piece of software communicating with its command-and-control server: post /malicious.php
User-Agent: Malicious Tool V 1.0
Host: www.rcalicious.com
The IOC documentation suggests the URL is the only part that could change.
Which of the following regular expressions would allow the systems administrator to determine if any of the company hosts are compromised, while reducing false positives?
- A . User-Agent: Malicious Tool.*
- B . www. malicious. com/malicious. php
- C . POST /malicious. php
- D . Hose: [a-2] *.malicious.com
- E . malicious. *
D
Explanation:
A regular expression (regex) is a sequence of characters that defines a search pattern for matching text. A regex can be used to detect the presence of a malicious piece of software communicating with its command-and-control server by matching the indicators of compromise (IOC) in the network traffic.
In this case, the systems administrator should use the regex Host: [a-z]*.malicious.com to determine if any of the company hosts are compromised, while reducing false positives, because this regex would:
Match the Host header in the HTTP request, which specifies the domain name of the command-and-control server.
Allow any subdomain under the malicious.com domain, by using the character class [a-z]*, which matches zero or more lowercase letters.
Escape the dot character in the domain name, by using the backslash, which prevents it from being interpreted as a wildcard that matches any character.
Not match any other parts of the IOC that could change, such as the URL path, the User-Agent header, or the HTTP method.
Based on PCI DSS v3.4, One Particular database field can store data, but the data must be unreadable.
Which of the following data objects meets this requirement?
- A . PAN
- B . CVV2
- C . Cardholder name
- D . expiration date
The Chief Information Security Officer (CISO) asked a security manager to set up a system that sends an alert whenever a mobile device enters a sensitive area of the company’s data center. The CISO would also like to be able to alert the individual who is entering the area that the access was logged and monitored.
Which of the following would meet these requirements?
- A . Near-field communication
- B . Short Message Service
- C . Geofencing
- D . Bluetooth
C
Explanation:
Geofencing is a location-based service that allows an organization to define and enforce a virtual boundary around a sensitive area, such as a data center. Geofencing can use various technologies, such as GPS, Wi-Fi, cellular data, or RFID, to detect when a mobile device enters or exits the geofence. Geofencing can also trigger certain actions or notifications based on the device’s location. For example, the organization can set up a geofencing policy that sends an alert to the CISO and the device user when a mobile device enters the data center area. Geofencing can also be used to restrict access to certain apps or features based on the device’s location.
Verified Reference:
https://developer.android.com/training/location/geofencing
https://www.manageengine.com/mobile-device-management/mdm-geofencing.html
https://www.koombea.com/blog/mobile-geofencing/
An e-commerce company is running a web server on premises, and the resource utilization is usually less than 30%. During the last two holiday seasons, the server experienced performance issues because of too many connections, and several customers were not able to finalize purchase orders. The company is looking to change the server configuration to avoid this kind of performance issue.
Which of the following is the MOST cost-effective solution?
- A . Move the server to a cloud provider.
- B . Change the operating system.
- C . Buy a new server and create an active-active cluster.
- D . Upgrade the server with a new one.
A
Explanation:
Moving the server to a cloud provider is the most cost-effective solution to avoid performance issues caused by too many connections during peak seasons, such as holidays. Moving the server to a cloud provider can provide scalability, elasticity, and availability for the web server, as it can adjust its resources and capacity according to the demand and traffic. Moving the server to a cloud provider can also reduce operational and maintenance costs, as the cloud provider can handle the infrastructure and security aspects. Changing the operating system may not help avoid performance issues, as it could introduce compatibility or functionality problems, and it may not address the resource or capacity limitations. Buying a new server and creating an active-active cluster may help avoid performance issues, but it may not be cost-effective, as it could involve hardware and software expenses, as well as complex configuration and management tasks. Upgrading the server with a new one may help avoid performance issues, but it may not be cost-effective, as it could involve hardware and software expenses, as well as migration and testing efforts.
Verified Reference:
https://www.comptia.org/blog/what-is-cloud-computing
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A company is developing a new service product offering that will involve the storage of personal health information. The Chief Information Security Officer (CISO) is researching the relevant compliance regulations.
Which of the following best describes the CISO’s action?
- A . Data retention
- B . Data classification
- C . Due diligence
- D . Reference framework
C
Explanation:
Comprehensive and Detailed Step by Step
Due diligence involves researching and understanding regulatory requirements (e.g., HIPAA) to ensure compliance for handling sensitive data like personal health information. Data retention refers to how long data is stored, not compliance research.
Data classification organizes data by sensitivity but is not specific to compliance research. Reference frameworks provide guidelines for implementation but are not directly about research.
Reference: CompTIA CASP+ Exam Objective 1.1: Analyze business and compliance requirements.
CASP+ Study Guide, 5th Edition, Chapter 2, Legal and Regulatory Compliance.
A company requires a task to be carried by more than one person concurrently. This is an example of:
- A . separation of d duties.
- B . dual control
- C . least privilege
- D . job rotation
B
Explanation:
Dual control is a security principle that requires two or more authorized individuals to perform a task concurrently. This reduces the risk of fraud, error, or misuse of sensitive assets or information.
Verified Reference:
https://www.comptia.org/training/books/casp-cas-004-study-guide, https://www.isaca.org/resources/isaca-journal/issues/2018/volume-1/using-dual-control-to-mitigate-risk
