Practice Free CAS-004 Exam Online Questions
An organization is moving its intellectual property data from on premises to a CSP and wants to secure the data from theft.
Which of the following can be used to mitigate this risk?
- A . An additional layer of encryption
- B . A third-party data integrity monitoring solution
- C . A complete backup that is created before moving the data
- D . Additional application firewall rules specific to the migration
A
Explanation:
The company should use an additional layer of encryption to secure the data from theft when moving to a CSP. Encryption is a process of transforming data into an unreadable format using a secret key. Encryption can protect the data from unauthorized access or modification during transit and at rest. Encryption can be applied at different levels, such as disk, file, or application. An additional layer of encryption can provide an extra security measure on top of the encryption provided by the CSP.
Verified Reference:
https://learn.microsoft.com/en-us/partner-center/transition-seat-based-services
https://cloud.google.com/architecture/patterns-for-connecting-other-csps-with-gcp
A company Is adopting a new artificial-intelligence-based analytics SaaS solution. This Is the company’s first attempt at using a SaaS solution, and a security architect has been asked to determine any future risks.
Which of the following would be the GREATEST risk In adopting this solution?
- A . The inability to assign access controls to comply with company policy
- B . The inability to require the service provider process data in a specific country
- C . The inability to obtain company data when migrating to another service
- D . The inability to conduct security assessments against a service provider
A large telecommunications equipment manufacturer needs to evaluate the strengths of security controls in a new telephone network supporting first responders.
Which of the following techniques would the company use to evaluate data confidentiality controls?
- A . Eavesdropping
- B . On-path
- C . Cryptanalysis
- D . Code signing
- E . RF sidelobe sniffing
A satellite communications ISP frequently experiences outages and degraded modes of operation over one of its legacy satellite links due to the use of deprecated hardware and software. Three days per week, on average, a contracted company must follow a checklist of 16 different high-latency commands that must be run in serial to restore nominal performance. The ISP wants this process to be automated.
Which of the following techniques would be BEST suited for this requirement?
- A . Deploy SOAR utilities and runbooks.
- B . Replace the associated hardware.
- C . Provide the contractors with direct access to satellite telemetry data.
- D . Reduce link latency on the affected ground and satellite segments.
A
Explanation:
Deploying SOAR (Security Orchestration Automation and Response) utilities and runbooks is the best technique for automating the process of restoring nominal performance on a legacy satellite link due to degraded modes of operation caused by deprecated hardware and software.
The Chief Information Security Officer (CISO) is working with a new company and needs a legal “document to ensure all parties understand their roles during an assessment.
Which of the following should the CISO have each party sign?
- A . SLA
- B . ISA
- C . Permissions and access
- D . Rules of engagement
D
Explanation:
Rules of engagement are legal documents that should be signed by all parties involved in an assessment to ensure they understand their roles and responsibilities. Rules of engagement define the scope, objectives, methods, deliverables, limitations, and expectations of an assessment project. They also specify the legal and ethical boundaries, communication channels, escalation procedures, and reporting formats for the assessment. Rules of engagement help to avoid misunderstandings, conflicts, or liabilities during or after an assessment.
Reference: [CompTIA CASP+ Study Guide, Second Edition, page 34]
A vulnerability analyst identified a zero-day vulnerability in a company’s internally developed software. Since the current vulnerability management system does not have any checks for this vulnerability, an engineer has been asked to create one.
Which of the following would be BEST suited to meet these requirements?
- A . ARF
- B . ISACs
- C . Node.js
- D . OVAL
D
Explanation:
OVAL (Open Vulnerability and Assessment Language) is a standard that would be best suited for creating checks for a zero-day vulnerability in an organization’s internally developed software. OVAL is a standard for expressing system configuration information and vulnerabilities in an XML format, allowing interoperability and automation among different security tools and platforms. An engineer can use OVAL to create definitions or tests for specific vulnerabilities or states in the software, and then use OVAL-compatible tools to scan or evaluate the software against those definitions or tests. ARF (Asset Reporting Format) is not a standard for creating checks for vulnerabilities, but a standard for expressing information about assets and their characteristics in an XML format, allowing interoperability and automation among different security tools and platforms. ISACs (Information Sharing and Analysis Centers) are not standards for creating checks for vulnerabilities, but organizations that collect, analyze, and disseminate information about threats, vulnerabilities, incidents, or best practices among different sectors or communities. Node.js is not a standard for creating checks for vulnerabilities, but a runtime environment that allows executing JavaScript code outside of a web browser, enabling the development of scalable web applications or services.
Verified Reference:
https://www.comptia.org/blog/what-is-oval
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
Company A is establishing a contractual with Company
B. The terms of the agreement are formalized in a document covering the payment terms, limitation of liability, and intellectual property rights.
Which of the following documents will MOST likely contain these elements
- A . Company A-B SLA v2.docx
- B . Company A OLA v1b.docx
- C . Company A MSA v3.docx
- D . Company A MOU v1.docx
- E . Company A-B NDA v03.docx
C
Explanation:
A MSA stands for master service agreement, which is a document that covers the general terms and conditions of a contractual relationship between two parties. It usually includes payment terms, limitation of liability, intellectual property rights, dispute resolution, and other clauses that apply to all services provided by one party to another.
Verified Reference:
https://www.comptia.org/training/books/casp-cas-004-study-guide, https://www.upcounsel.com/master-service-agreement
An architectural firm is working with its security team to ensure that any draft images that are leaked to the public can be traced back to a specific external party.
Which of the following would BEST accomplish this goal?
- A . Properly configure a secure file transfer system to ensure file integrity.
- B . Have the external parties sign non-disclosure agreements before sending any images.
- C . Only share images with external parties that have worked with the firm previously.
- D . Utilize watermarks in the images that are specific to each external party.
D
Explanation:
Watermarking is a technique of adding an identifying image or pattern to an original image to protect its ownership and authenticity. Watermarks can be customized to include specific information about the external party, such as their name, logo, or date of receipt. This way, if any draft images are leaked to the public, the firm can trace back the source of the leak and take appropriate actions.
Verified Reference:
https://en.wikipedia.org/wiki/Watermark
https://www.canva.com/features/watermark-photos/
https://www.mdpi.com/2078-2489/11/2/110
A software development company is building a new mobile application for its social media platform. The company wants to gain its users’ trust by re reducing the risk of on-path attacks between the mobile client and its servers and by implementing stronger digital trust.
To support users’ trust, the company has released the following internal guidelines:
* Mobile clients should verify the identity of all social media servers locally.
* Social media servers should improve TLS performance of their certificate status.
+ Social media servers should inform the client to only use HTTPS.
Given the above requirements, which of the following should the company implement? (Select TWO).
- A . Quick UDP internet connection
- B . OCSP stapling
- C . Private CA
- D . DNSSEC
- E . CRL
- F . HSTS
- G . Distributed object model
B,F
Explanation:
OCSP stapling and HSTS are the best options to meet the requirements of reducing the risk of on-path attacks and implementing stronger digital trust. OCSP stapling allows the social media servers to improve TLS performance by sending a signed certificate status along with the certificate, eliminating the need for the client to contact the CA separately. HSTS allows the social media servers to inform the client to only use HTTPS and prevent downgrade attacks. The other options are either irrelevant or less effective for the given scenario.
A security analyst needs to recommend a remediation to the following threat:
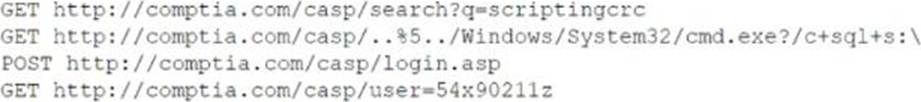
Which of the following actions should the security analyst propose to prevent this successful exploitation?
- A . Patch the system.
- B . Update the antivirus.
- C . Install a host-based firewall.
- D . Enable TLS 1.2.
