Practice Free CAS-004 Exam Online Questions
A security architect works for a manufacturing organization that has many different branch offices. The architect is looking for a way to reduce traffic and ensure the branch offices receive the latest copy of revoked certificates issued by the CA at the organization’s headquarters location. The solution must also have the lowest power requirement on the CA.
Which of the following is the BEST solution?
- A . Deploy an RA on each branch office.
- B . Use Delta CRLs at the branches.
- C . Configure clients to use OCSP.
- D . Send the new CRLs by using GPO.
C
Explanation:
Reference: https://www.sciencedirect.com/topics/computer-science/revoke-certificate
OCSP (Online Certificate Status Protocol) is a protocol that allows clients to check the revocation status of certificates in real time by querying an OCSP responder server. This would enable the organization to determine whether it is vulnerable to the active campaign utilizing a specific vulnerability, as it would show if any certificates have been compromised or revoked. Deploying an RA (registration authority) on each branch office may not help with checking the revocation status of certificates, as an RA is responsible for verifying the identity of certificate applicants, not issuing or revoking certificates. Using Delta CRLs (certificate revocation lists) at the branches may not provide timely or accurate information on certificate revocation status, as CRLs are updated periodically and may not reflect the latest changes. Implementing an inbound BGP (Border Gateway Protocol) prefix list may not help with checking the revocation status of certificates, as BGP is a protocol for routing network traffic between autonomous systems, not verifying certificates.
Verified Reference:
https://www.comptia.org/blog/what-is-ocsp
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A security analyst is designing a touch screen device so users can gain entry into a locked room by touching buttons numbered zero through nine in a specific numerical sequence. The analyst designs the keypad so that the numbers are randomly presented to the user each time the device is used.
Which of the following best describes the design trade-offs? (Select two.)
- A . The risk of someone overseeing a pattern as a user enters the numbers is decreased.
- B . The routines to generate the random sequences are trivial to implement.
- C . This design makes entering numbers more difficult for users.
- D . The device needs to have additional power to compute the numbers.
- E . End users will have a more difficult time remembering the access numbers.
- F . Weak or easily guessed access numbers are more likely.
A,C
Explanation:
Step by Step
A: Randomizing the keypad reduces the risk of shoulder-surfing attacks by eliminating predictable patterns.
C: Randomization increases the cognitive load on users, making it harder to input numbers quickly.
D: Additional computational power is minimal and not typically a trade-off.
E and F: Remembering access numbers or weak passwords are unrelated to keypad randomization.
Reference: CASP+ Exam Objectives 3.4 C Evaluate usability and security trade-offs in design.
The Chief information Officer (CIO) wants to establish a non-banding agreement with a third party that outlines the objectives of the mutual arrangement dealing with data transfers between both organizations before establishing a format partnership.
Which of the follow would MOST likely be used?
- A . MOU
- B . OLA
- C . NDA
- D . SLA
A security analyst notices a number of SIEM events that show the following activity:
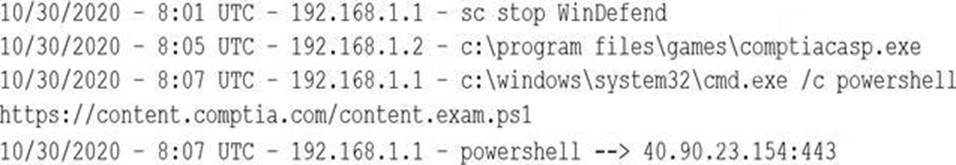
Which of the following response actions should the analyst take FIRST?
- A . Disable powershell.exe on all Microsoft Windows endpoints.
- B . Restart Microsoft Windows Defender.
- C . Configure the forward proxy to block 40.90.23.154.
- D . Disable local administrator privileges on the endpoints.
C
Explanation:
The SIEM events show that powershell.exe was executed on multiple endpoints with an outbound connection to 40.90.23.154, which is an IP address associated with malicious activity. This could indicate a malware infection or a command-and-control channel. The best response action is to configure the forward proxy to block 40.90.23.154, which would prevent further communication with the malicious IP address. Disabling powershell.exe on all endpoints may not be feasible or effective, as it could affect legitimate operations and not remove the malware. Restarting Microsoft Windows Defender may not detect or stop the malware, as it could have bypassed or disabled it. Disabling local administrator privileges on the endpoints may not prevent the malware from running or communicating, as it could have escalated privileges or used other methods.
Verified Reference:
https://www.comptia.org/blog/what-is-a-forward-proxy
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
The Chief Information Security Officer is concerned about the possibility of employees downloading ‘malicious files from the internet and ‘opening them on corporate workstations.
Which of the following solutions would be BEST to reduce this risk?
- A . Integrate the web proxy with threat intelligence feeds.
- B . Scan all downloads using an antivirus engine on the web proxy.
- C . Block known malware sites on the web proxy.
- D . Execute the files in the sandbox on the web proxy.
D
Explanation:
Executing the files in the sandbox on the web proxy is the best solution to reduce the risk of employees downloading and opening malicious files from the internet. A sandbox is a secure and isolated environment that can run untrusted or potentially harmful code without affecting the rest of the system. By executing the files in the sandbox, the web proxy can analyze their behavior and detect any malicious activity before allowing them to reach the corporate workstations.
Reference: [CompTIA CASP+ Study Guide, Second Edition, page 273]
In a shared responsibility model for PaaS, which of the following is a customer’s responsibility?
- A . Network security
- B . Physical security
- C . OS security
- D . Host infrastructure
C
Explanation:
In a shared responsibility model for PaaS, the customer’s responsibility is OS security. PaaS stands for Platform as a Service, which is a cloud service model that provides a platform for customers to develop, run, and manage applications without having to deal with the underlying infrastructure.
The cloud provider is responsible for the physical security, network security, and host infrastructure of the platform, while the customer is responsible for the security of the operating system, the application, and the data. The customer needs to ensure that the operating system is patched, configured, and protected from malware and unauthorized access.
Verified Reference:
https://learn.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility
https://www.techtarget.com/searchcloudcomputing/feature/The-cloud-shared-responsibility-model-for-IaaS-PaaS-and-SaaS
https://www.splunk.com/en_us/blog/learn/shared-responsibility-model.html
Which of the following should an organization implement to prevent unauthorized API key sharing?
- A . OTP
- B . Encryption
- C . API gateway
- D . HSM
C
Explanation:
An API gateway is a management tool that sits between a client and a collection of backend services. It acts as a reverse proxy to accept all application programming interface (API) calls, aggregate the various services required to fulfill them, and return the appropriate result. API gateways can enforce policies such as rate limiting and authentication to prevent unauthorized access, making it an effective solution to prevent unauthorized API key sharing. By managing APIs at the gateway level, organizations can ensure that API keys are used as intended and are not shared or misused, addressing the need for secure management of API keys.
A control systems analyst is reviewing the defensive posture of engineering workstations on the shop floor.
Upon evaluation, the analyst makes the following observations:
• Unsupported, end-of-life operating systems were still prevalent on the shop floor.
• There are no security controls for systems with supported operating systems.
• There is little uniformity of installed software among the workstations.
Which of the following would have the greatest impact on the attack surface?
- A . Deploy antivirus software to all of the workstations.
- B . Increase the level of monitoring on the workstations.
- C . Utilize network-based allow and block lists.
- D . Harden all of the engineering workstations using a common strategy.
D
Explanation:
Hardening the engineering workstations using a consistent strategy would have the greatest impact on reducing the attack surface. The workstations are running outdated and unsupported operating systems, with no security controls, and inconsistent software installations, which significantly increases the risk of exploitation. Hardening involves applying patches, reducing unnecessary software, disabling unused services, and ensuring uniform security controls across all systems. By addressing these vulnerabilities and inconsistencies, the overall security posture improves significantly, which aligns with CASP+ best practices on reducing attack surfaces by standardizing and securing endpoint configurations.
Reference: CASP+ CAS-004 Exam Objectives: Domain 1.0 C Risk Management (Vulnerability Management, System Hardening)
CompTIA CASP+ Study Guide: Hardening Techniques and Attack Surface Reduction
An application developer is including third-party background security fixes in an application. The fixes seem to resolve a currently identified security issue. However, when the application is released to the public, report come In that a previously vulnerability has returned.
Which of the following should the developer integrate into the process to BEST prevent this type of behavior?
- A . Peer review
- B . Regression testing
- C . User acceptance
- D . Dynamic analysis
A software developer created an application for a large, multinational company. The company is concerned the program code could be reverse engineered by a foreign entity and intellectual property would be lost.
Which of the following techniques should be used to prevent this situation?
- A . Obfuscation
- B . Code signing
- C . Watermarking
- D . Digital certificates
A
Explanation:
Obfuscation is a technique used to make the program code difficult to understand or read. It can help to prevent reverse engineering by making it more challenging to analyze the code and understand its structure and functionality, thereby protecting intellectual property.
