Practice Free CAS-004 Exam Online Questions
A security analyst is validating the MAC policy on a set of Android devices. The policy was written to ensure non-critical applications are unable to access certain resources.
When reviewing dmesg, the analyst notes many entries such as:
Despite the deny message, this action was still permit following is the MOST likely fix for this issue?
- A . Add the objects of concern to the default context.
- B . Set the devices to enforcing
- C . Create separate domain and context files for irc.
- D . Rebuild the policy, reinstall, and test.
A security consultant needs to set up wireless security for a small office that does not have Active Directory. Despite the lack of central account management, the office manager wants to ensure a high level of defense to prevent brute-force attacks against wireless authentication.
Which of the following technologies would BEST meet this need?
- A . Faraday cage
- B . WPA2 PSK
- C . WPA3 SAE
- D . WEP 128 bit
C
Explanation:
WPA3 SAE prevents brute-force attacks.
“WPA3 Personal (WPA-3 SAE) Mode is a static passphrase-based method. It provides better security than what WPA2 previously provided, even when a non-complex password is used, thanks to Simultaneous Authentication of Equals (SAE), the personal authentication process of WPA3.”
An organization is implementing a new identity and access management architecture with the following objectives:
Supporting MFA against on-premises infrastructure
Improving the user experience by integrating with SaaS applications
Applying risk-based policies based on location
Performing just-in-time provisioning
Which of the following authentication protocols should the organization implement to support these requirements?
- A . Kerberos and TACACS
- B . SAML and RADIUS
- C . OAuth and OpenID
- D . OTP and 802.1X
C
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/migrate-application-authentication-to-azure-active-directory
O Auth and OpenID are two authentication protocols that can support the objectives of the organization.
O Auth is a protocol that allows users to grant access to their resources on one site (or service) to another site (or service) without sharing their credentials. OpenID is a protocol that allows users to use an existing account to sign in to multiple websites without creating new passwords. Both protocols can support MFA, SaaS integration, risk-based policies, and just-in-time provisioning.
Reference: https://auth0.com/docs/protocols/oauth2 https://openid.net/connect/
An organization is implementing a new identity and access management architecture with the following objectives:
Supporting MFA against on-premises infrastructure
Improving the user experience by integrating with SaaS applications
Applying risk-based policies based on location
Performing just-in-time provisioning
Which of the following authentication protocols should the organization implement to support these requirements?
- A . Kerberos and TACACS
- B . SAML and RADIUS
- C . OAuth and OpenID
- D . OTP and 802.1X
C
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/migrate-application-authentication-to-azure-active-directory
O Auth and OpenID are two authentication protocols that can support the objectives of the organization.
O Auth is a protocol that allows users to grant access to their resources on one site (or service) to another site (or service) without sharing their credentials. OpenID is a protocol that allows users to use an existing account to sign in to multiple websites without creating new passwords. Both protocols can support MFA, SaaS integration, risk-based policies, and just-in-time provisioning.
Reference: https://auth0.com/docs/protocols/oauth2 https://openid.net/connect/
An administrator completed remediation for all the findings of a penetration test and notifies the management team that the systems are ready to be placed back into production.
Which of the following steps should the management team require the analyst to perform immediately before placing the systems back into production?
- A . Rescan for corrections/changes.
- B . Conduct the entire penetration test again.
- C . Harden the targeted systems.
- D . Ensure a host-based IPS is in place.
A
Explanation:
Rescanning ensures all identified vulnerabilities have been resolved and no additional changes introduced new issues. This step is critical for verifying remediation effectiveness before moving systems back into production, aligning with CASP+ objective 5.1, which involves verifying security measures during testing and evaluation phases.
A security analyst discovered that a database administrator’s workstation was compromised by malware. After examining the Jogs. the compromised workstation was observed connecting to multiple databases through ODBC.
The following query behavior was captured:
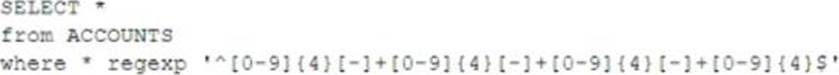
Assuming this query was used to acquire and exfiltrate data, which of the following types of data was compromised, and what steps should the incident response plan contain?
- A . Personal health information: Inform the human resources department of the breach and review the DLP logs.
В. Account history; Inform the relationship managers of the breach and create new accounts for the affected users. - B . Customer IDs: Inform the customer service department of the breach and work to change the account numbers.
- C . PAN: Inform the legal department of the breach and look for this data in dark web monitoring.
A developer wants to develop a secure external-facing web application. The developer is looking for an online community that produces tools, methodologies, articles, and documentation in the field of web-application security
Which of the following is the BEST option?
- A . ICANN
- B . PCI DSS
- C . OWASP
- D . CSA
- E . NIST
A security analyst identified a vulnerable and deprecated runtime engine that is supporting a public-facing banking application. The developers anticipate the transition to modern development environments will take at least a month.
Which of the following controls would best mitigate the risk without interrupting the service during the transition?
- A . Shutting down the systems until the code is ready
- B . Uninstalling the impacted runtime engine
- C . Selectively blocking traffic on the affected port
- D . Configuring IPS and WAF with signatures
D
Explanation:
Given the vulnerability in the deprecated runtime engine, configuring an IPS (Intrusion Prevention System) and WAF (Web Application Firewall) with appropriate signatures is the best temporary control. This allows the organization to monitor and block potential attacks targeting known vulnerabilities in the runtime engine while the developers work on the transition. Shutting down the systems or uninstalling the runtime engine would cause service interruptions, and blocking traffic might disrupt legitimate users. IPS and WAF provide an active layer of defense without interrupting service. CASP+ emphasizes the use of layered security, including IPS and WAF, to mitigate risks in public-facing applications.
Reference: CASP+ CAS-004 Exam Objectives: Domain 3.0 C Enterprise Security Architecture (Web Application Firewalls, Intrusion Prevention Systems)
CompTIA CASP+ Study Guide: Mitigating Application Vulnerabilities with WAFs and IPS
A security engineer investigates an incident and determines that a rogue device is on the network. Further investigation finds that an employee’s personal device has been set up to access company resources and does not comply with standard security controls.
Which of the following should the security engineer recommend to reduce the risk of future reoccurrence?
- A . Require device certificates to access company resources.
- B . Enable MFA at the organization’s SSO portal.
- C . Encrypt all workstation hard drives.
- D . Hide the company wireless SSID.
A
Explanation:
To reduce the risk of unauthorized devices accessing company resources, requiring device certificates is an effective control. Device certificates can be used to authenticate devices before they are allowed to connect to the network and access resources, ensuring that only devices with a valid certificate, which are typically managed and issued by the organization, can connect.
An auditor Is reviewing the logs from a web application to determine the source of an Incident. The web application architecture Includes an Internet-accessible application load balancer, a number of web servers. In a private subnet, application servers, and one database server In a tiered configuration. The application load balancer cannot store the logs.
The following are sample log snippets:
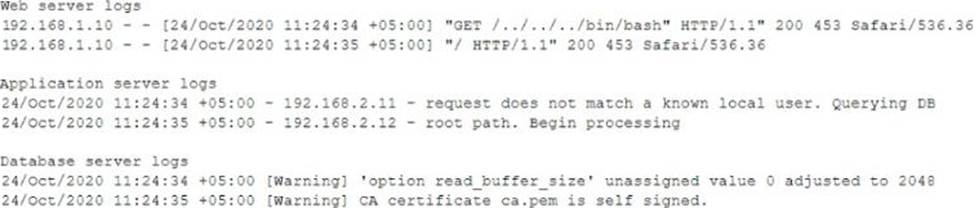
Which of the following should the auditor recommend to ensure future incidents can be traced back to the sources?
- A . Enable the x-Forwarded-For header al the load balancer.
- B . Install a software-based HIDS on the application servers.
- C . Install a certificate signed by a trusted CA.
- D . Use stored procedures on the database server.
- E . Store the value of the $_server ( ‘ REMOTE_ADDR ‘ ] received by the web servers.
