Practice Free 350-401 Exam Online Questions
What is a Type 1 hypervisor?
- A . runs directly on a physical server and depends on a previously installed operating system
- B . runs directly on a physical server and includes its own operating system
- C . runs on a virtual server and depends on an already installed operating system
- D . run on a virtual server and includes its own operating system.
Which language can be used to model configuration and state data?
- A . JSON
- B . XML
- C . XDR
- D . YANG
What is used by vManage to interact with Cisco SD-WAN devices in the fabric?
- A . northbound API
- B . RESTCONF
- C . Southbound API
- D . IPsec
Which method ensures the confidentiality of data exchanged over a REST API?
- A . Use TLS to secure the underlying HTTP session.
- B . Use me POST method Instead or URL-encoded GET to pass parameters.
- C . Deploy digest-based authentication to protect the access to the API.
- D . Encode sensitive data using Base64 encoding.
DRAG DROP
Drag anti drop the characteristics from the ten onto the configuration models on the right.

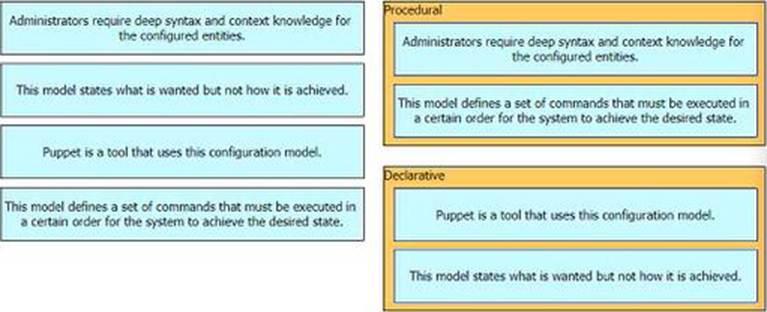
Which characteristic applies to Cisco SD-Access?
- A . It uses dynamic routing the discover and provision access switches.
- B . It uses VXLAN for the control plane
- C . It uses VXLAN for the data plane
- D . It uses dynamic routing to discover and provision border switches
SIMULATION 15:

R1
config t
flow record NetFlow-Record
match ipv4 source address
match ipv4 destination address
collect country bytes
flow exporter NetFlow-Exporter
destination 10.10.1.10
transport udp 9996
flow monitor NetFlow-Monitor
record NetFlow-Record
exporter NetFlow-Exporter
exit
int et0/0
ip flow monitor NetFlow-Monitor input
ip sla 1
http get http://10.10.1.100
frequency 600
exit
ip sla schedule 1 start-time now
wr
Sw1
config t
monitor session 2 source int e0/0
monitor session 2 source int et0/2
monitor session 2 destination interface e1/0
wr
Refer to the exhibit.

Assuming the WLC’s interfaces are not in the same subnet as the RADIUS server, which interface would the WLC use as the source for all RADIUS-related traffic?
- A . the interface specified on the WLAN configuration
- B . any interface configured on the WLC
- C . the controller management interface
- D . the controller virtual interface
DRAG DROP
Drag and drop the code snippets from the bottom onto the blanks in the code to construct a request that configures a deny rule on an access list?

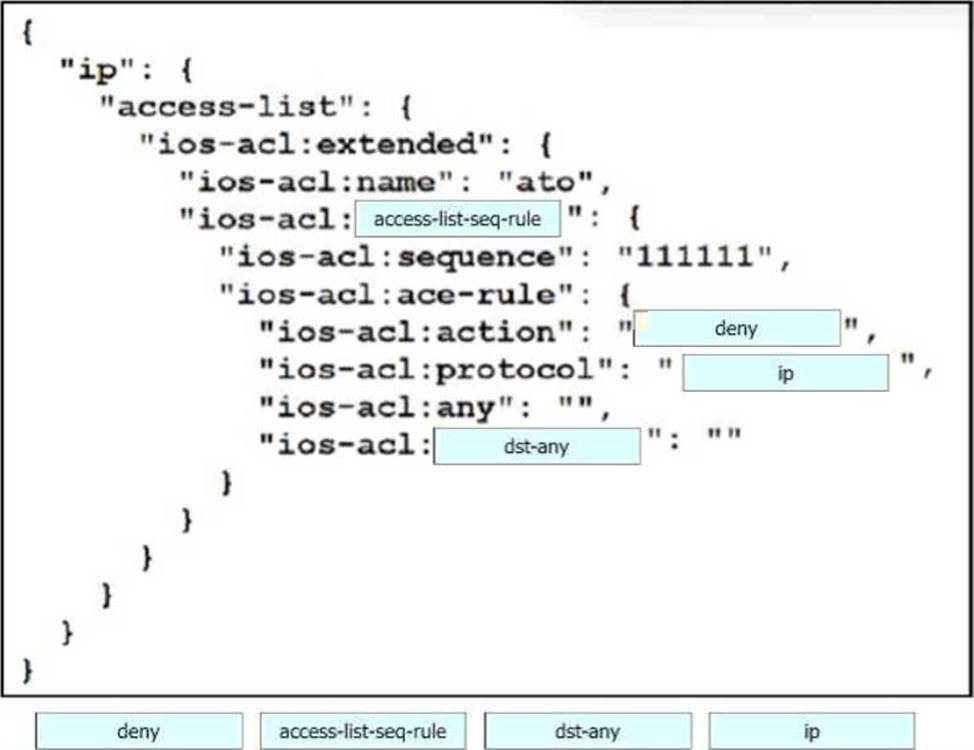
Explanation:
access-list-sec-rule, deny, ip, dst-any
Which next generation firewall feature supports separate security services for multiple departments?
- A . state sharing mode to .trade the user data sessions and replication to the neighbor firewall using a failover link
- B . Layer 3 mode with resource tracking capabilities and automatic configuration synchronization between the nodes and security zones
- C . multicontext mode with specific logical or physical interface allocation within each context and grouped into security zones
- D . virtual switch mode to provide traffic inspection capabilities for the flows entering the firewall and dropping packets based on policy configuration
