Practice Free 300-710 Exam Online Questions
What is an advantage of adding multiple inline interface pairs to the same inline interface set when deploying an asynchronous routing configuration?
- A . Allows the IPS to identify inbound and outbound traffic as part of the same traffic flow.
- B . The interfaces disable auto negotiation and interface speed is hard coded set to 1000 Mbps.
- C . Allows traffic inspection to continue without interruption during the Snort process restart.
- D . The interfaces are automatically configured as a media-independent interface crossover.
A
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/firepower/601/configuration/guide/fpmc-config-guide-v601/fpmc-config-guide-v60_chapter_01011010.pdf
Which feature within the Cisco FMC web interface allows for detecting, analyzing and blocking malware in network traffic?
- A . intrusion and file events
- B . Cisco AMP for Endpoints
- C . Cisco AMP for Networks
- D . file policies
DRAG DROP
Drag and drop the configuration steps from the left into the sequence on the right to enable external authentication on Cisco FMC to a RADIUS server.

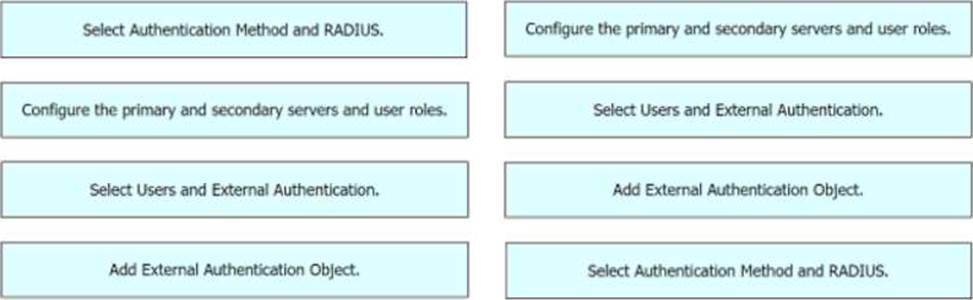
Explanation:
4,1,2,3
A network administrator is migrating from a Cisco ASA to a Cisco FTD. EIGRP is configured on the Cisco ASA but it is not available in the Cisco FMC.
Which action must the administrator take to enable this feature on the Cisco FTD?
- A . Configure EIGRP parameters using FlexConfig objects.
- B . Add the command feature eigrp via the FTD CLI.
- C . Create a custom variable set and enable the feature in the variable set.
- D . Enable advanced configuration options in the FMC.
A network administrator needs to create a policy on Cisco Firepower to fast-path traffic to avoid
Layer 7 inspection. The rate at which traffic is inspected must be optimized.
What must be done to achieve this goal?
- A . Enable lhe FXOS for multi-instance.
- B . Configure a prefilter policy.
- C . Configure modular policy framework.
- D . Disable TCP inspection.
A network engineer is planning on replacing an Active/Standby pair of physical Cisco Secure Firewall ASAs with a pair of Cisco Secure Firewall Threat Defense Virtual appliances.
Which two virtual environments support the current High Availability configuration? (Choose two.)
- A . KVM
- B . Azure
- C . ESXi
- D . AWS
- E . Openstack
CD
Explanation:
Cisco Secure Firewall Threat Defense Virtual (FTDv) appliances support High Availability (HA) configurations in specific virtual environments. The supported environments for HA setups include: ESXi: VMware’s ESXi is a widely supported platform for deploying FTDv appliances in HA configurations.
AWS: Amazon Web Services (AWS) supports FTDv appliances and allows for HA configurations to ensure redundancy and reliability in cloud deployments.
These environments provide the necessary infrastructure and capabilities to support the high availability requirements for FTDv appliances.
Reference: Cisco Secure Firewall Threat Defense Virtual Configuration Guide, Chapter on High Availability and Supported Platforms.
An engineer is troubleshooting connectivity to the DNS servers from hosts behind a new Cisco FTD device. The hosts cannot send DNS queries to servers in the DMZ.
Which action should the engineer take to troubleshoot this issue using the real DNS packets?
- A . Use the Connection Events dashboard to check the block reason and adjust the inspection policy as needed.
- B . Use the packet capture tool to check where the traffic is being blocked and adjust the access control or intrusion policy as needed.
- C . Use the packet tracer tool to determine at which hop the packet is being dropped.
- D . Use the show blocks command in the Threat Defense CLI tool and create a policy to allow the blocked traffic.
A Cisco FTD device is running in transparent firewall mode with a VTEP bridge group member ingress interface.
What must be considered by an engineer tasked with specifying a destination MAC address for a packet trace?
- A . Only the UDP packet type is supported.
- B . The output format option for the packet logs is unavailable.
- C . The destination MAC address is optional if a VLAN ID value is entered.
- D . The VLAN ID and destination MAC address are optional.
A network administrator is concerned about (he high number of malware files affecting users’ machines.
What must be done within the access control policy in Cisco FMC to address this concern?
- A . Create an intrusion policy and set the access control policy to block.
- B . Create an intrusion policy and set the access control policy to allow.
- C . Create a file policy and set the access control policy to allow.
- D . Create a file policy and set the access control policy to block.
An organization is configuring a new Cisco Firepower High Availability deployment.
Which action must be taken to ensure that failover is as seamless as possible to end users?
- A . Set up a virtual failover MAC address between chassis.
- B . Use a dedicated stateful link between chassis.
- C . Load the same software version on both chassis.
- D . Set the same FQDN for both chassis.
