Practice Free 300-710 Exam Online Questions
Which Cisco Firepower Threat Defense, which two interface settings are required when configuring a routed interface? (Choose two.)
- A . Redundant Interface
- B . EtherChannel
- C . Speed
- D . Media Type
- E . Duplex
CE
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/firepower/610/fdm/fptd-fdm-config-guide-610/fptd-fdm-interfaces.html
Which connector is used to integrate Cisco ISE with Cisco FMC for Rapid Threat Containment?
- A . pxGrid
- B . FTD RTC
- C . FMC RTC
- D . ISEGrid
An engineer is troubleshooting an intermittent connectivity issue on a Cisco Secure Firewall Threat Defense appliance and must collect 24 hours’ worth of data. The engineer started a packet capture. Whenever it stops prematurely during this time period. The engineer notices that the packet capture butter size is set to the default of 32 MB.
Which butter S170 is the maximum that the engineer must sot to able the packet capture to run successfully?
- A . 64 MB
- B . 1GB
- C . 10 GB
- D . 100 GB
B
Explanation:
To collect 24 hours’ worth of data using a packet capture on a Cisco Secure Firewall Threat Defense (FTD) appliance without prematurely stopping due to buffer size limitations, the engineer should increase the packet capture buffer size. The default buffer size is 32 MB, which is insufficient for extended captures.
Steps:
Access the packet capture configuration on the FTD device.
Increase the buffer size to 1 GB, which provides a significantly larger capacity for capturing packets over a 24-hour period.
Setting the buffer size to 1 GB should accommodate a substantial amount of traffic and prevent the capture from stopping prematurely.
Reference: Cisco Secure Firewall Threat Defense Configuration Guide, Chapter on Packet Capture Configuration and Management.
DRAG DROP
A network engineer is deploying a Cisco Firepower 4100 appliance and must configure a multi-instance environment for high availability.
Drag and drop me actions from the left into sequence on the right far this configuration.

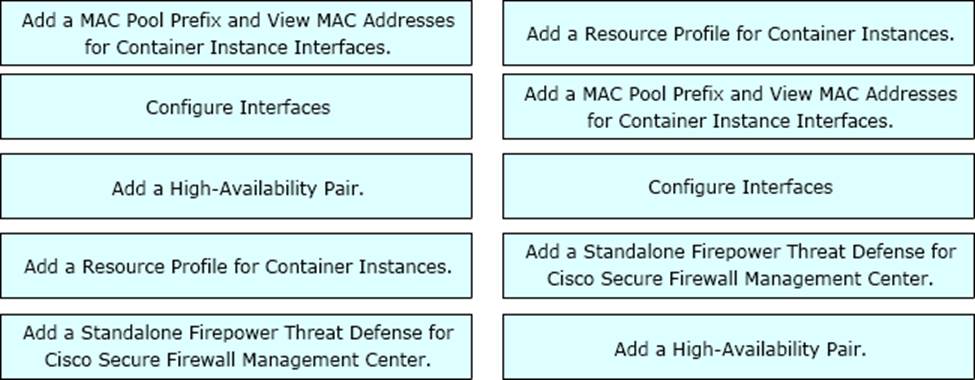
Explanation:
The correct sequence of actions for configuring a multi-instance environment for high availability on a Cisco Firepower 4100 appliance is as follows:
Add a resource profile for container instances. A resource profile defines the CPU, RAM, and disk space allocation for each container instance. You can create multiple resource profiles with different resource settings and assign them to different container instances1.
Add a MAC pool prefix and view the MAC address for the container instance interfaces. A MAC pool prefix is a 24-bit prefix that is used to generate MAC addresses for the container instance interfaces.
You can specify a custom MAC pool prefix or use the default one. You can also view the MAC addresses that are assigned to each container instance interface1.
Configure interfaces. You need to configure the physical interfaces, EtherChannels, and VLAN subinterfaces that will be used by the container instances. You can also configure shared interfaces that can be used by multiple container instances on the same security module/engine1.
Add a Standalone Firepower Threat Defense for Cisco Secure Firewall Management Center. You need to add a logical device that runs a standalone Firepower Threat Defense (FTD) application instance and register it with the Cisco Secure Firewall Management Center (FMC). This logical device will act as the management interface for the container instances1.
Add a high-availability pair. You need to add another logical device that runs a standalone FTD application instance and register it with the FMC as well. Then, you need to configure high availability (HA) between the two standalone FTD logical devices. This will enable HA for the container instances that are associated with them1.
There is an increased amount of traffic on the network and for compliance reasons, management needs visibility into the encrypted traffic.
What is a result of enabling TLS’SSL decryption to allow this visibility?
- A . It prompts the need for a corporate managed certificate
- B . It has minimal performance impact
- C . It is not subject to any Privacy regulations
- D . It will fail if certificate pinning is not enforced
A network administrator is trying to convert from LDAP to LDAPS for VPN user authentication on a Cisco FTD.
Which action must be taken on the Cisco FTD objects to accomplish this task?
- A . Add a Key Chain object to acquire the LDAPS certificate.
- B . Create a Certificate Enrollment object to get the LDAPS certificate needed.
- C . Identify the LDAPS cipher suite and use a Cipher Suite List object to define the Cisco FTD connection requirements.
- D . Modify the Policy List object to define the session requirements for LDAPS.
Which CLI command is used to generate firewall debug messages on a Cisco Firepower?
- A . system support firewall-engine-debug
- B . system support ssl-debug
- C . system support platform
- D . system support dump-table
A
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/212330-firepower-management-center-display-acc.html
The administrator notices that there is malware present with an .exe extension and needs to verify if any of the systems on the network are running the executable file.
What must be configured within Cisco AMP for Endpoints to show this data?
- A . prevalence
- B . threat root cause
- C . vulnerable software
- D . file analysis
A network engineer is logged into the Cisco AMP for Endpoints console and sees a malicious verdict for an identified SHA-256 hash.
Which configuration is needed to mitigate this threat?
- A . Add the hash to the simple custom deletion list.
- B . Use regular expressions to block the malicious file.
- C . Enable a personal firewall in the infected endpoint.
- D . Add the hash from the infected endpoint to the network block list.
Which command is entered in the Cisco FMC CLI to generate a troubleshooting file?
- A . show running-config
- B . show tech-support chassis
- C . system support diagnostic-cli
- D . sudo sf_troubleshoot.pl
D
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/sourcefire-defense-center/117663-technote-SourceFire-00.html
