Practice Free 300-710 Exam Online Questions
Upon detecting a flagrant threat on an endpoint, which two technologies instruct Cisco Identity Services Engine to contain the infected endpoint either manually or automatically? (Choose two.)
- A . Cisco ASA 5500 Series
- B . Cisco FMC
- C . Cisco AMP
- D . Cisco Stealthwatch
- E . Cisco ASR 7200 Series
An administrator is attempting to remotely log into a switch in the data centre using SSH and is unable to connect.
How does the administrator confirm that traffic is reaching the firewall?
- A . by running Wireshark on the administrator’s PC
- B . by performing a packet capture on the firewall.
- C . by running a packet tracer on the firewall.
- D . by attempting to access it from a different workstation.
The network administrator wants to enhance the network security posture by enabling machine learning tor malware detection due to a concern with suspicious Microsoft executable file types that were seen while creating monthly security reports for the CIO.
Which feature must be enabled to accomplish this goal?
- A . Spero
- B . dynamic analysis
- C . static analysis
- D . Ethos
Refer to the exhibit.
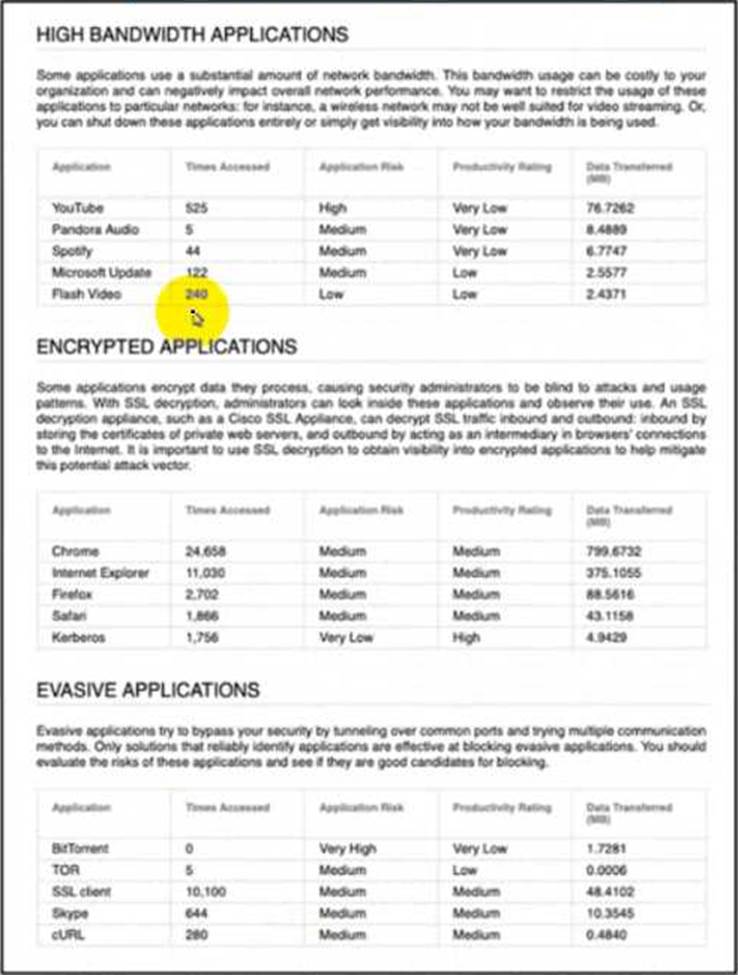
An engineer is analyzing a Network Risk Report from Cisco FMC.
Which application must the engineer take immediate action against to prevent unauthorized network use?
- A . Kerberos
- B . YouTube
- C . Chrome
- D . TOR
A network administrator is configuring Snort inspection policies and is seeing failed deployment messages in Cisco FMC.
What information should the administrator generate for Cisco TAC to help troubleshoot?
- A . A "show tech" file for the device in question.
- B . A "troubleshoot" file for the device in question.
- C . A "troubleshoot" file for the Cisco FMC.
- D . A "show tech" for the Cisco FMC.
An engineer is monitoring network traffic from their sales and product development departments, which are on two separate networks.
What must be configured in order to maintain data privacy for both departments?
- A . Use a dedicated IPS inline set for each department to maintain traffic separation
- B . Use 802 1Q mime set Trunk interfaces with VLANs to maintain logical traffic separation
- C . Use passive IDS ports for both departments
- D . Use one pair of inline set in TAP mode for both departments
Which two types of objects are reusable and supported by Cisco FMC? (Choose two.)
- A . dynamic key mapping objects that help link HTTP and HTTPS GET requests to Layer 7 application protocols.
- B . reputation-based objects that represent Security Intelligence feeds and lists, application filters based on category and reputation, and file lists
- C . network-based objects that represent IP address and networks, port/protocols pairs, VLAN tags, security zones, and origin/destination country
- D . network-based objects that represent FQDN mappings and networks, port/protocol pairs, VXLAN tags, security zones and origin/destination country
- E . reputation-based objects, such as URL categories
BC
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmc-config-guide-v62/reusable_objects.html#ID-2243-00000414
A network administrator registered a new FTD to an existing FMC. The administrator cannot place the FTD in transparent mode.
Which action enables transparent mode?
- A . Add a Bridge Group Interface to the FTD before transparent mode is configured.
- B . Dereglster the FTD device from FMC and configure transparent mode via the CLI.
- C . Obtain an FTD model that supports transparent mode.
- D . Assign an IP address to two physical interfaces.
An engineer is configuring a custom intrusion rule on Cisco FMC. The engineer needs the rule to search the payload or stream for the string "|45 5* 26 27 4 0A|*.
Which Keyword must the engineer use with this stung lo create an argument for packed inspection?
- A . metadata
- B . Content
- C . Protected _ content
- D . data
B
Explanation:
The content keyword is used to specify a string or pattern to search for in the payload or stream of a packet. The string must be enclosed in quotation marks and can use modifiers such as nocase, depth, offset, and so on. The string can also use hexadecimal notation by using a pipe symbol (|) before and after the hexadecimal characters.
For example, content:"|45 5* 26 27 4 0A|" will match any payload or stream that contains the hexadecimal bytes 45 5 26 27 4 0A followed by any number of bytes2
Refer to the Exhibit.

A security engineer must improve security in an organization and is producing a risk mitigation strategy to present to management for approval.
Which action must the security engineer take based on this Attacks Risk Report?
- A . Inspect DNS traffic
- B . Block NetBIOS.
- C . Block Internal Explorer
- D . Inspect TCP port 80 traffic
A
Explanation:
Based on the Attacks Risk Report, DNS is associated with a high number of impact events (16). DNS traffic is critical for network operations but can also be exploited for malicious activities such as DNS tunneling, DDoS attacks, and data exfiltration. To improve security, the security engineer should focus on inspecting DNS traffic. This involves deploying DNS security solutions and monitoring DNS traffic for anomalies to detect and mitigate potential threats.
Steps:
Implement DNS security tools such as DNS filtering, DNSSEC, and DNS anomaly detection.
Configure the firewall to inspect DNS traffic for malicious activities.
Regularly analyze DNS logs to identify and respond to threats.
This action addresses a significant risk identified in the report and helps to mitigate potential attacks exploiting DNS.
Reference: Cisco Secure Firewall Management Center Administrator Guide, Chapter on DNS Security and Traffic Inspection.
