Practice Free 2V0-51.23 Exam Online Questions
The administrator of Windows 10 desktops in a VMware Horizon environment needs to build a new Windows 10 desktop pool. This new pool will be dedicated to training and onboarding new employees. The administrator has created a shortcut on a test machine, which has successfully opened the web browser to the on-boarding applications. After deploying the new desktop pool across the company, the administrator notices that the shortcut placed on desktops is not available to any other user connecting to the desktop pool.
Which two options are available for the administrator to make this shortcut available to all desktop pool users, while minimizing ongoing administrative effort, before updating the desktop pool golden image? (Choose two.)
- A . Copy the shortcut during user provisioning to a non-writeable App Volume.
- B . Copy the shortcut to the Windows Default Domain Controller Policy.
- C . Copy the shortcut to c:usersPublicDesktop.
- D . Configure a Shortcut with Horizon View Client.
- E . Configure a Shortcut with DEM (Dynamic Environment Manager).
C, E
Explanation:
The two options that are available for the administrator to make the shortcut available to all desktop pool users, while minimizing ongoing administrative effort, before updating the desktop pool golden image are:
– Copy the shortcut to c:usersPublicDesktop. This option will place the shortcut in the public desktop folder, which is shared by all users who log on to the same computer. The public desktop folder is normally a hidden folder, so the administrator needs to enable the option to show hidden files and folders in File Explorer1. This option does not require any additional software or configuration, but it will only work for the existing desktops in the pool. If new desktops are added or refreshed, the shortcut will not be copied automatically.
– Configure a Shortcut with DEM (Dynamic Environment Manager). This option will use the DEM console to create a shortcut configuration that will apply the shortcut to the user’s desktop during logon2. The administrator needs to install and configure DEM on the Horizon environment, and create a configuration share and a profile archive share for storing the DEM settings3. This option requires more initial setup, but it will work for any desktop in the pool, regardless of whether it is new or refreshed. It also allows more flexibility and control over the shortcut properties and conditions.
The other options are not valid or feasible because:
– Copying the shortcut during user provisioning to a non-writeable App Volume will not work because App Volumes are used to deliver applications, not shortcuts. App Volumes are virtual disks that are attached to the virtual machines at runtime, and they contain application files, registry entries, and settings4. Copying a shortcut to an App Volume will not make it appear on the user’s desktop.
– Copying the shortcut to the Windows Default Domain Controller Policy will not work because this policy is used to configure settings for domain controllers, not desktops. The Default Domain Controller Policy is a Group Policy Object (GPO) that is linked to the Domain Controllers organizational unit (OU) in Active Directory, and it contains security settings that are applied to all domain controllers in the domain5. Copying a shortcut to this policy will not affect any desktops in the Horizon environment.
– Configuring a Shortcut with Horizon View Client will not work because Horizon View Client is used to connect to remote desktops and applications, not to create shortcuts. Horizon View Client is a software application that runs on various devices and platforms, and it allows users to access their virtual desktops and applications through a secure connection6. Configuring a shortcut with Horizon View Client will not make it appear on the user’s desktop.
References:
– How to make a desktop shortcut available for all users in Windows 101
– VMware Dynamic Environment Manager (DEM) 2306 C Carl Stalhood2
– VMware Tech Zone Antivirus Considerations in a VMware Horizon Environment: exclusions for Horizon View, App Volumes, User Environment Manager, ThinApp3
– App Volumes Overview
– Default Domain Controller Policy5
– VMware Horizon Clients Documentation6
When integrating a Linux OS based desktop into Active Directory, which three of the following can be used? (Choose three.)
- A . OpenLDAP Server Pass-through authentication
- B . Winbind Domain Join
- C . OpenLDAP Server Cut-through authentication
- D . Windows Domain Join
- E . System Security Services Daemon (SSSD) LDAP authentication against the AD
BDE
Explanation:
Integrating a Linux OS-based desktop into Active Directory can be achieved using Winbind for domain joining and authentication, Windows Domain Join through tools like Samba, and System Security Services Daemon (SSSD) for LDAP authentication against Active Directory. These methods enable Linux desktops to participate in a Windows-centric environment, allowing for centralized authentication and management.
Which two options describe how an administrator can access the settings and status of a pool? (Choose two.)
- A . Navigate to Inventory > Machines > click on a vCenter > in the Summary section check the Pool Settings section.
- B . Navigate to Inventory > Desktops > click on a Pool > in the Summary section check the Pool Settings section.
- C . Navigate to Inventory > Desktops > click on a Pool > in the Summary section check the vCenter Server section, to verify the status of the image during pool deployment.
- D . Navigate to Inventory > Machines > click on a vCenter > in the Desktop Pool section check the Pool
Settings section.
BC
Explanation:
To access the settings and status of a pool in VMware Horizon, an administrator would navigate to the Inventory > Desktops section of the Horizon Console. By selecting a specific pool, the administrator can view detailed information in the Summary section, including Pool Settings and the status of the image used during the pool’s deployment, providing insights into the pool’s configuration and operational status.
An administrator needs to enable Session Collaboration in the VMware Horizon environment.
What will be used as a requirement to enable Session Collaboration?
- A . floating Instant Clone pool
- B . dedicated Instant Clone pool
- C . PCoIP protocol
- D . BLAST protocol
D
Explanation:
Collaboration is a feature that allows users to invite other users to join an existing Windows or Linux remote desktop session with both screen sharing and audio out features enabled. A remote desktop session that is shared in this way is called a collaborative session. The user that shares a session with another user is called the session owner, and the user that joins a shared session is called a session collaborator. A Horizon administrator must enable the Session Collaboration feature for the desktop pool or farm that contains the remote desktops that support collaboration.
One of the requirements to enable Session Collaboration is to use the VMware Blast display protocol for the remote desktops. VMware Blast is a protocol that provides high-performance, high-quality graphics and multimedia delivery over LAN or WAN networks. VMware Blast supports Session Collaboration by allowing multiple users to view and interact with the same remote desktop session simultaneously. Other display protocols, such as PCoIP or RDP, do not support Session Collaboration and will not allow users to share or join collaborative sessions.
Therefore, to enable Session Collaboration in the VMware Horizon environment, the administrator needs to use the BLAST protocol as a requirement.
Reference: Configuring Session Collaboration, Sharing Remote Desktop Sessions, and [VMware Horizon 8.x Professional Course]
What are two Cloud Pod Architecture feature limitations? (Choose two.)
- A . Cloud Pod Architecture does not support Active Directory two-way trusts between domains.
- B . Cloud Pod Architecture is not supported with Unified Access Gateway appliances.
- C . Kiosk mode clients are not supported unless a workaround has been implemented.
- D . Cloud Pod Architecture cannot span multiple sites and data centers simultaneously.
- E . The Cloud Pod Architecture feature is not supported in an IPv6 environment.
AC
Explanation:
Cloud Pod Architecture is a feature that allows administrators to link multiple Horizon pods across sites and data centers to form a single logical entity called a pod federation. Cloud Pod Architecture enables global entitlements, which allow users to access desktops and applications from any pod in the pod federation. Cloud Pod Architecture also provides load balancing, high availability, and disaster recovery capabilities for Horizon deployments.
However, Cloud Pod Architecture has some feature limitations that administrators should be aware of. Two of these limitations are:
– Cloud Pod Architecture does not support Active Directory two-way trusts between domains: This means that the domains that contain the Horizon pods in the pod federation must have a one-way trust relationship, where the domain that contains the Cloud Pod Architecture home site trusts all the other domains, but not vice versa. A two-way trust relationship, where each domain trusts and is trusted by all the other domains, is not supported by Cloud Pod Architecture and can cause authentication and entitlement issues.
– Kiosk mode clients are not supported unless a workaround has been implemented: This means that users who log in to Horizon Client in kiosk mode, which is a mode that allows users to access a single desktop or application without entering credentials, cannot access desktops or applications from a Cloud Pod Architecture implementation. Kiosk mode clients are not compatible with global entitlements and load balancing features of Cloud Pod Architecture. However, there is a workaround that involves creating a dedicated user account and a dedicated desktop pool for each kiosk mode client and using a script to launch Horizon Client with the appropriate parameters. For instructions, see VMware Knowledge Base (KB) article 21488881.
The other options are not limitations of Cloud Pod Architecture:
– Cloud Pod Architecture is supported with Unified Access Gateway appliances: Unified Access Gateway is a platform that provides secure edge services for Horizon deployments, such as secure remote access, load balancing, and authentication. Unified Access Gateway is compatible with Cloud Pod Architecture and can be configured to route user requests to the appropriate pod in the pod federation based on global entitlements and load balancing policies.
– Cloud Pod Architecture can span multiple sites and data centers simultaneously: This is one of the main benefits of Cloud Pod Architecture, as it allows administrators to scale up and out their Horizon deployments across different geographic locations and network boundaries. Cloud Pod Architecture can support up to 15 pods per pod federation andup to 5 sites per pod federation, with a maximum of 200,000 sessions per pod federation.
– The Cloud Pod Architecture feature is supported in an IPv6 environment: IPv6 is the latest version of the Internet Protocol that provides a larger address space and enhanced security features for network communication. Cloud Pod Architecture supports IPv6 environments and can operate in mixed IPv4 and IPv6 environments as well.
References: Cloud Pod Architecture Limitations in Horizon 8 and [VMware Horizon 8.x Professional Course]
HOTSPOT
Refer to the exhibit.
An administrator wants to be able to see the desktop VM’s active session in vSphere Console.
In the Group Policy Management Editor window, mark the correct VMware Blast setting to be configured by clicking on it.

In the list shown, there is no specific setting under "VMware Blast" that directly allows for the monitoring of active sessions in the vSphere Console. Typically, active session monitoring in the vSphere Console is not solely managed via Group Policy but also involves settings within the VMware Horizon Console itself and the vSphere infrastructure.
If the task requires enabling something from Group Policy for better visibility or performance tracking of the VM’s active sessions, then the closest relevant setting in the context of VMware Blast would be the "VMware Horizon Performance Tracker" if it was listed or part of another category in the Group Policy settings.
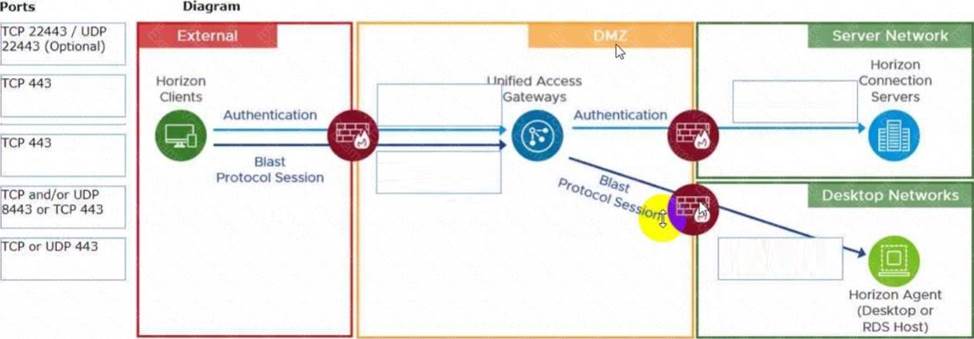
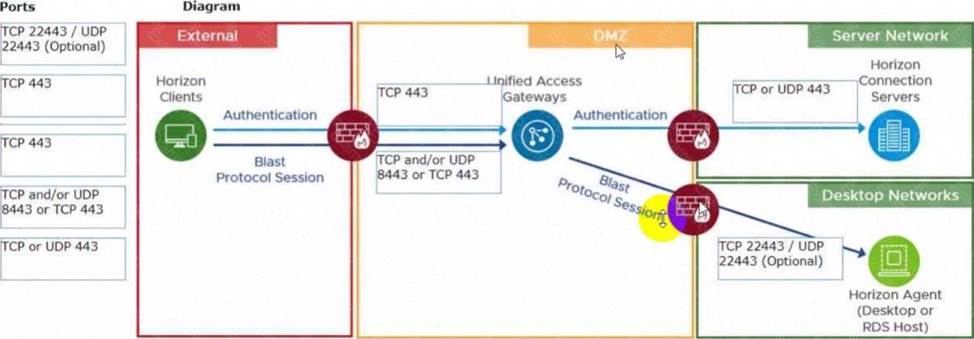
DRAG DROP
Refer to the exhibit.
Drag and drop the ports on the left to allow an external Blast Extreme connection through Unified Access Gateway (UAG) into the diagram on the right.
To reduce the risk of users downloading malware to the corporate network, an administrator wants to allow end-users to open only intranet websites inside their virtual desktop. Additionally, the administrator wants to configure all other URLs to automatically open in a browser on the end-user’s client machine.
Which steps should the administrator take to meet the requirements? (Choose two.)
- A . Enable the URL Content Redirection feature in Horizon Agent.
- B . Disable the Allow External Website feature in Horizon Agent.
- C . Enable secure website settings in the Global Settings Security menu.
- D . Configure group policy settings to indicate how Horizon Agent redirects the URL
- E . Enable the URL Content Redirection feature on the desktop pool settings.
A, D
Explanation:
The URL Content Redirection feature allows administrators to configure specific URLs to open on the client machine or in a remote desktop or published application. This can help reduce the risk of users downloading malware to the corporate network, as well as improve the user experience and performance of certain web applications.
To meet the requirements of the scenario, the administrator needs to enable the URL Content Redirection feature in Horizon Agent when installing or upgrading it on the instant-clone desktops. This will allow Horizon Agent to send or receive URLs from Horizon Client, depending on the redirection direction. The administrator also needs to configure group policy settings to indicate how Horizon Agent redirects the URL. Specifically, the administrator needs to enable agent-to-client redirection, which means that Horizon Agent sends the URL to Horizon Client, which opens the default application for the protocol in the URL on the client machine. The administrator also needs to specify which URLs are redirected from a remote desktop to a client, and which URLs are not redirected. In this case, the administrator needs to configure a whitelist of intranet websites that are allowed to open inside the virtual desktop, and a blacklist of all other websites that are automatically redirected to a browser on the client machine.
The other options are not relevant or sufficient for meeting the requirements. Disabling the Allow External Website feature in Horizon Agent will prevent users from accessing any external websites from their virtual desktops, which might not be desirable or practical. Enabling secure website settings in the Global Settings Security menu will not affect how URLs are redirected, but only how secure connections are established between Horizon components. Enabling the URL Content Redirection feature on the desktop pool settings will not work unless it is also enabled in Horizon Agent and configured with group policy settings.
Reference: Configuring URL Content Redirection and [VMware Horizon 8.x Professional Course]
Which two scenarios are appropriate for a cloud implementation of a VDI solution over an on-premises solution? (Choose two.)
- A . The organization already has infrastructure to support a VDI.
- B . The organization needs to setup high availability and disaster recovery.
- C . The organization needs to quickly scale-up in disparate geographical locations.
- D . The organization has limited CapEx budget.
- E . The organization controls highly confidential data.
CD
Explanation:
A cloud implementation of a VDI solution over an on-premises solution is appropriate for the following scenarios:
– The organization needs to quickly scale-up in disparate geographical locations. A cloud VDI solution can provide faster provisioning, deployment, and management of virtual desktops and applications across multiple regions and data centers. A cloud VDI solution can also offer better performance, availability, and user experience for remote and mobile workers who need to access their desktops and applications from anywhere and any device12.
– The organization has limited CapEx budget. A cloud VDI solution can reduce the upfront capital expenditure (CapEx) required to purchase, install, and maintain the hardware and software infrastructure for a VDI solution. A cloud VDI solution can also lower the operational expenditure (OpEx) by shifting the responsibility of managing, updating, and securing the VDI infrastructure to the cloud provider. A cloud VDI solution can offer flexible and predictable pricing models based on usage, subscription, or consumption13.
The other scenarios are not appropriate for a cloud implementation of a VDI solution over an on-premises solution because:
– The organization already has infrastructure to support a VDI. If the organization has already invested in the hardware and software resources to support a VDI solution, it may not be cost-effective or feasible to migrate to a cloud VDI solution. The organization may also have existing policies, processes, and workflows that are tailored to the on-premises VDI solution and may not be compatible with the cloud VDI solution4.
– The organization needs to setup high availability and disaster recovery. While a cloud VDI solution can provide high availability and disaster recovery capabilities, it may not be sufficient or reliable for some organizations that have strict requirements for data protection, compliance, and business continuity. An on-premises VDI solution can offermore control, customization, and security over the backup, replication, and restoration of the VDI data and applications in the event of a disaster5.
– The organization controls highly confidential data. A cloud VDI solution may pose some risks or challenges for organizations that handle sensitive or regulated data, such as financial, healthcare, or government data. A cloud VDI solution may not meet the compliance standards or regulations that apply to the organization’s data. A cloud VDI solution may also expose the organization’s data to potential breaches, leaks, or unauthorized access by third parties. An on-premises VDI solution can provide more visibility, governance, and encryption over the organization’s data6.
References: =
1: VMware: What is Desktop as a Service (DaaS)?
2: Parallels: VDI in the Cloud: Which Cloud VDI Product Is Right for You?
3: Microsoft Azure: What Is Virtual Desktop Infrastructure (VDI)?
4: VMware: On-Premise vs Cloud: Which is Better for Your Business?
5: VMware: Disaster Recovery Solutions for Virtual Desktop Infrastructure (VDI)
6: Microsoft Azure: Virtual desktop infrastructure security best practices
An administrator needs to configure BLAST Bandwidth Profiles to define the quality, maximum session bandwidth, and frame rate.
Which are the two possible ways an administrator can accomplish this goal? (Choose two.)
- A . Create a login script which will set all required settings in the desktop.
- B . Use post-synchronization scripts during pool creation to define these settings.
- C . Configure these BLAST settings in the desktop pool configuration.
- D . Use Horizon Smart Policies of Dynamic Environment Manager.
- E . Set all required settings from a profile manually through GPO policies.
DE
Explanation:
Configuring BLAST Bandwidth Profiles involves setting quality, maximum session bandwidth, and frame rate controls. This can be effectively managed using Horizon Smart Policies within VMware’s Dynamic Environment Manager (DEM), which allows administrators to create contextual policies that
dynamically adapt to the end-user’s environment. Alternatively, Group Policy Objects (GPOs) can be used to manually set these configurations across the desktop environment, providing a more static approach to enforcing these settings.
