Practice Free 2V0-21.23 Exam Online Questions
An administrator is tasked with migrating a single virtual machine (VM) from an existing VMware vCenter to a secure environment where corporate security policy requires that all VMs be encrypted. The secure environment consists of a dedicated vCenter instance with a 4-node vSphere cluster and already contains a number of encrypted VMs.
Which two steps must the administrator take to ensure the migration is a success? (Choose two.)
- A . Ensure that the source and destination vCenter instances share the same Key Management Server (KMS).
- B . Ensure that Encrypted vMotion is turned off for the VM.
- C . Ensure that the VM is encrypted before attempting the migration.
- D . Ensure that the VM is powered off before attempting the migration.
- E . Ensure that the source and destination vCenter Servers have a different Key Management Server (KMS).
Which two tasks can be completed using vSphere LifeCycle Manager? (Choose two.)
- A . Manage the firmware lifecycle of ESXi hosts that are part of a managed cluster with a single image.
- B . Check that the ESXi hosts are compliant with the recommended baseline and update the hosts.
- C . Upgrade VMware vCenter from version 7 to 8.
- D . Check the hardware compatibility of the hosts in a cluster against the VMware Compatibility Guide (VCG) using baselines.
- E . Manage the firmware lifecycle of ESXi hosts are part of a managed cluster using baselines.
Refer to the exhibit.
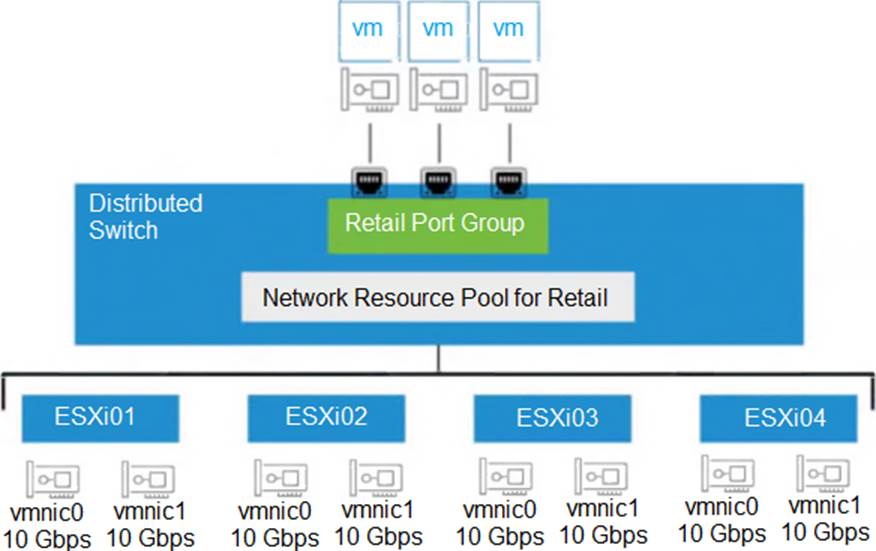
An administrator set up the following configuration:
• The distributed switch has four ESXi hosts, and each host has two 10 Gbps NICs.
• In the Network I/O Control configuration, the amount of bandwidth reserved for virtual machine (VM) traffic if 4 Gbps.
The administrator wants to guarantee that VMs in the Retail distributed port group can access 50 percent of the available reserved bandwidth for VM traffic.
Given this scenario, what should the size (in Gbps) of the Retail network resource pool be?
- A . 40
- B . 32
- C . 8
- D . 16
Allow vSphere Lifecycle Manager to automatically control maintenance mode on the ESXi hosts.
An administrator wants to use tag-based placement rules on their virtual machine disks using VMware vCenter.
Which option would allow the administrator to achieve this?
- A . Storage Policy Based Management
- B . Storage I/O Control
- C . vSphere Storage APIs for Storage Awareness (VASA)
- D . vSphere Distributed Resource Scheduler (DRS)
An administrator successfully installs VMware ESXi onto the first host of a new vSphere cluster but makes no additional configuration changes.
When attempting to log into the vSphere Host Client using the Fully Qualified Domain Name (FQDN) of the host, the administrator receives the following error message:
“Server Not Found C We can’t connect to the server at esxi101.corp.local.”
The following information has been provided to complete the configuration:
Host FQDN: esxi101.corp.local –
Management VLAN ID: 10 –
DHCP: No –
Management IP Address: 172.16.10.101 / 24
Management IP Gateway: 172.16.10.1
Corporate DNS Servers: 172.16.10.5, 172.16.10.6
ONS Domain: corp.local –
In addition, all host configurations must also meet the following requirements:
The management network must use only IPv4 network protocols.
The management network must be fault tolerant.
Which three high level tasks should the administrator complete, at a minimum, in order to successfully log into the vSphere Host Client using the FQDN for esxi101 and complete the configuration? (Choose three.)
- A . Ensure a DNS A Record is created for the VMware ESXi host on the corporate DNS servers.
- B . Update the VMware ESXi Management Network DNS configuration to use the corporate DNS servers for names resolution.
- C . Update the VMware ESXi Management Network IPv4 configuration to use a static a IPv4 address.
- D . Configure at least two network adapters for the VMware ESXi Management Network.
- E . Set the value of the VMware ESXi Management Network VLAN ID to 10.
- F . Disable IPv6 for the VMware ESXi Management Network.
A group of new virtual machines have been deployed using thin-provisioned disks due to the limited storage space available in an environment. The storage team has expressed concern about extensive use of this type of provisioning.
An administrator is tasked with creating a custom alarm to notify the storage team when thin provisioning reaches a certain capacity threshold.
Where must the administrator define this alarm?
- A . Datastore
- B . Data center
- C . Datastore cluster
- D . Virtual machine
An administrator is asked to configure a security policy at the port group level of a standard switch.
The following requirements must be met:
The security policy must apply to all virtual machines on portgroup-1.
All traffic must be forwarded, regardless of the destination.
Which security policy must the administrator configure?
- A . Forged transmits set to reject
- B . MAC address changes set to accept
- C . Promiscuous mode set to reject
- D . Promiscuous mode set to accept
An administrator is asked to configure a security policy at the port group level of a standard switch.
The following requirements must be met:
The security policy must apply to all virtual machines on portgroup-1.
All traffic must be forwarded, regardless of the destination.
Which security policy must the administrator configure?
- A . Forged transmits set to reject
- B . MAC address changes set to accept
- C . Promiscuous mode set to reject
- D . Promiscuous mode set to accept
A vSphere cluster has the following vSphere Distributed Resource Scheduler (DRS) group configuration:
Virtual machine (VM) group named DB
Host groups named PROD11 and PROD55
The administrator wants to force the VMs in the DB group to run on the hosts in the PROD11 group. However, if all the hosts in PROD11 go offline for maintenance, then the VMs in the DB group should run on hosts in PROD55.
Which VM/Host rule must the administrator create to ensure that these requirements are met?
- A . A preferential rule between the DB group and the PROD11 group
- B . A preferential rule between the DB group and the PROD55 group
- C . A required rule between the DB group and the PROD11 group
- D . A required rule between the DB group and the PROD55 group
