Practice Free 200-201 Exam Online Questions
One of the objectives of information security is to protect the CIA of information and systems.
What does CIA mean in this context?
- A . confidentiality, identity, and authorization
- B . confidentiality, integrity, and authorization
- C . confidentiality, identity, and availability
- D . confidentiality, integrity, and availability
D
Explanation:
CIA stands for confidentiality, integrity, and availability, which are the three main objectives of information security. Confidentiality means protecting the information from unauthorized access or disclosure. Integrity means ensuring the information is accurate and consistent, and preventing unauthorized modification or deletion. Availability means ensuring the information and systems are accessible and usable by authorized users when needed.
Reference: https://learningnetworkstore.cisco.com/on-demand-e-learning/understanding-cisco-cybersecurity-operations-fundamentals-cbrops-v1.0/CSCU-LP-CBROPS-V1-028093.html (Module 2: Security Concepts, Lesson 2.1: Security Principles)
What do host-based firewalls protect workstations from?
- A . zero-day vulnerabilities
- B . unwanted traffic
- C . malicious web scripts
- D . viruses
B
Explanation:
Host-based firewalls are designed to protect individual workstations from unwanted traffic by filtering incoming and outgoing network communications based on predefined security rules. They can block unauthorized access attempts and prevent potentially harmful traffic from reaching the system.
Refer to the exhibit.
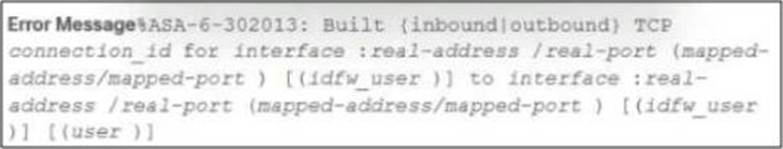
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events.
Which technology provided these logs?
- A . antivirus
- B . proxy
- C . IDS/IPS
- D . firewall
D
Explanation:
The logs indicating multiple local TCP connection events are typically provided by a firewall. Firewalls are responsible for monitoring and controlling incoming and outgoing network traffic based on predetermined security rules, and they generate logs that detail such events, which can be used for further analysis and incident response.
Reference: = Cisco Cybersecurity Operations Fundamentals
Which statement describes indicators of attack?
- A . internal hosts communicate with countries outside of the business range.
- B . Phishing attempts on an organization are blocked by mall AV.
- C . Critical patches are missing.
- D . A malicious file is detected by the AV software.
A
Explanation:
Indicators of Attack (IoA) refer to observable behaviors or artifacts that suggest a security breach or ongoing attack.
When internal hosts communicate with countries outside the business range, it may indicate data exfiltration or command-and-control communication to an external threat actor.
Unlike Indicators of Compromise (IoC) which indicate that a system has already been compromised, IoAs are often used to identify malicious activity in its early stages.
Monitoring for unusual outbound connections is a crucial aspect of detecting advanced persistent
threats (APTs) and other sophisticated attacks.
Reference: Difference Between Indicators of Compromise and Indicators of Attack Cyber Threat Detection Using Indicators of Attack Network Monitoring for Anomalous Behavior
Which category relates to improper use or disclosure of PII data?
- A . legal
- B . compliance
- C . regulated
- D . contractual
B
Explanation:
The improper use or disclosure of Personally Identifiable Information (PII) falls under the category of compliance because organizations are required to adhere to laws and regulations that protect the privacy and security of PII. This includes following guidelines set forth by privacy laws such as GDPR, HIPAA, and others that mandate the proper handling of personal data to prevent misuse and unauthorized access123.
Reference: = Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS), Personally identifiable information (PII): What it is, how it’s used, and how to protect it, What is PII? Examples, laws, and standards, Overview of the Privacy Act: 2020 Edition
Which regular expression is needed to capture the IP address 192.168.20.232?
- A . ^ (?:[0-9]{1,3}.){3}[0-9]{1,3}
- B . ^ (?:[0-9]f1,3}.){1,4}
- C . ^ (?:[0-9]{1,3}.)’
- D . ^ ([0-9]-{3})
A
Explanation:
The regular expression ^ (?:[0-9]{1,3}.){3}[0-9]{1,3} is needed to capture the IP address
Which event is user interaction?
- A . gaining root access
- B . executing remote code
- C . reading and writing file permission
- D . opening a malicious file
D
Explanation:
User interaction is any event that requires the user to perform an action that enables or facilitates a cyberattack. Opening a malicious file is an example of user interaction, as it can trigger the execution of malicious code or malware that can compromise the system or network. Gaining root access, executing remote code, and reading and writing file permissions are not user interactions, but rather actions that can be performed by an attacker after exploiting a vulnerability or bypassing security controls.
Reference: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) – Cisco, More than 99% of cyberattacks rely on human interaction
An investigator is examining a copy of an ISO file that is stored in CDFS format.
What type of evidence is this file?
- A . data from a CD copied using Mac-based system
- B . data from a CD copied using Linux system
- C . data from a DVD copied using Windows system
- D . data from a CD copied using Windows
A
Explanation:
CDFS stands for Compact Disc File System, which is a file system used by Mac OS to store data on CDs. CDFS is also known as ISO 9660, which is a standard format for data interchange on optical discs. CDFS allows files to be accessed by different operating systems, such as Windows, Linux, and Mac OS. Therefore, an ISO file that is stored in CDFS format is data from a CD copied using Mac-based system.
Reference: = Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) v1.0, Module 4: Network Intrusion Analysis, Lesson 4.4: File Type Analysis, Topic 4.4.1: File Systems, page 4-40.
Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
- A . Display
- B . Man-in-the-middle
- C . Distributed denial of service
- D . Denial of service
C
Explanation:
A Distributed Denial of Service (DDoS) attack involves multiple compromised devices (botnet) sending a large number of requests to a target server to overwhelm it.
In a specific type of DDoS attack known as an NTP amplification attack, the attacker exploits the Network Time Protocol (NTP) servers by sending small queries with a spoofed source IP address (the target’s IP).
The NTP server responds with a much larger reply to the target’s IP address, thereby amplifying the traffic directed at the target.
This reflection and amplification technique significantly increases the volume of traffic sent to the
target, causing denial of service.
Reference: OWASP DDoS Attack Overview
NTP Amplification Attack Explained
Understanding Botnets and Distributed Attacks
Which evasion method involves performing actions slower than normal to prevent detection?
- A . timing attack
- B . traffic fragmentation
- C . resource exhaustion
- D . tunneling
B
Explanation:
Traffic fragmentation is an evasion technique where an attacker splits malicious payloads into smaller packets. This can help avoid detection since some security systems may not reassemble these packets to inspect the complete payload.
