Practice Free 200-201 Exam Online Questions
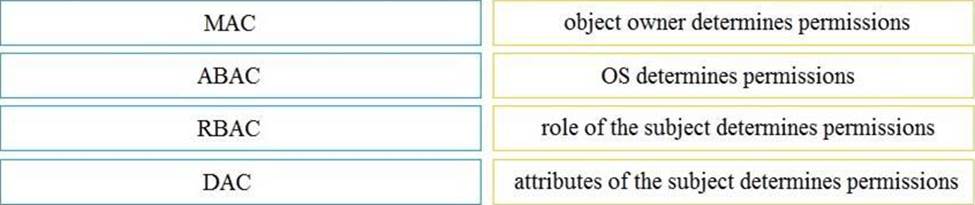
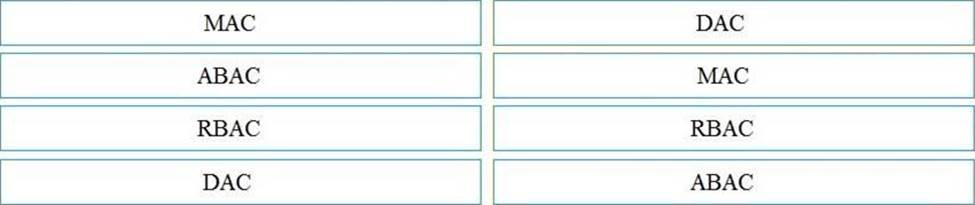
DRAG DROP
Drag and drop the access control models from the left onto the correct descriptions on the right.
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
- A . known-plaintext
- B . replay
- C . dictionary
- D . man-in-the-middle
D
Explanation:
A man-in-the-middle attack occurs when a third party intercepts and potentially alters the communication between two parties (in this case, two IP phones) without them knowing. This type of attack can lead to eavesdropping, where the attacker can gain unauthorized access to sensitive data being communicated between the two parties.
Reference: = Cisco Cybersecurity Operations Fundamentals – Module 5: Endpoint Threat Analysis and Computer Forensics
Which utility blocks a host portscan?
- A . HIDS
- B . sandboxing
- C . host-based firewall
- D . antimalware
C
Explanation:
A host-based firewall is a utility that can block unauthorized access to a computer system, including port scans. It monitors incoming and outgoing network traffic and permits or blocks data packets based on a set of security rules.
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
- A . forgery attack
- B . plaintext-only attack
- C . ciphertext-only attack
- D . meet-in-the-middle attack
C
Explanation:
When a stream cipher like RC4 is used twice with the same key, it becomes vulnerable to a ciphertext-only attack. In this type of attack, the attacker has access to several ciphertexts that are encrypted with the same key but does not know anything about the plaintexts. By analyzing these ciphertexts, an attacker can gain insights into the plaintext or even recover parts or all of it.
Reference: = Cisco Cybersecurity source documents or study guide (I need to search for specific references as I don’t have direct access to Cisco’s proprietary content)
Refer to the exhibit.
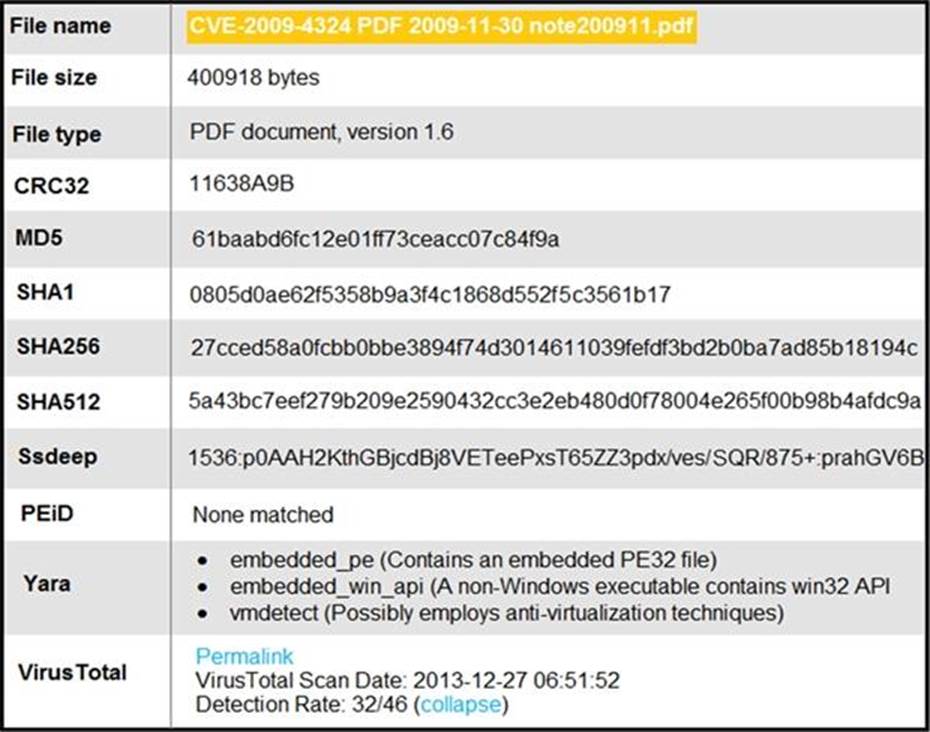
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email.
What is the state of this file?
- A . The file has an embedded executable and was matched by PEiD threat signatures for further analysis.
- B . The file has an embedded non-Windows executable but no suspicious features are identified.
- C . The file has an embedded Windows 32 executable and the Yara field lists suspicious features for further analysis.
- D . The file was matched by PEiD threat signatures but no suspicious features are identified since the signature list is up to date.
What is the practice of giving an employee access to only the resources needed to accomplish their job?
- A . principle of least privilege
- B . organizational separation
- C . separation of duties
- D . need to know principle
A
Explanation:
The principle of least privilege is a security best practice that states that an employee should have access to only the minimum amount of resources and permissions needed to perform their job function. This principle reduces the attack surface and the potential damage that can be caused by a compromised account, a malicious insider, or human error. The principle of least privilege can be enforced by using role-based access control (RBAC) and regular audits.
Reference: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) – Cisco, page 1-10; 200-201 CBROPS – Cisco, exam topic 1.2.a
DRAG DROP

Drag and drop the element names from the left onto the corresponding pieces of the PCAP file on the right.


Refer to the exhibit.

Which alert is identified from this packet capture?
- A . man-in-the-middle attack
- B . ARP poisoning
- C . brute-force attack
- D . SQL injection
C
Explanation:
The screenshot shows multiple POP requests with the command PASS, which is typically used for password entry. The rapid succession and variation of these requests suggest an attempt to guess the password, characteristic of a brute-force attack. Remember, always verify with additional data or context when possible, as packet captures can contain vast amounts of information and may require thorough analysis for accurate interpretation.
What is the principle of defense-in-depth?
- A . Agentless and agent-based protection for security are used.
- B . Several distinct protective layers are involved.
- C . Access control models are involved.
- D . Authentication, authorization, and accounting mechanisms are used.
B
Explanation:
Defense-in-depth is a security strategy where multiple layers of defense are placed throughout an information technology (IT) system. It addresses physical, technical, and administrative controls to provide redundancy and ensure that if one layer fails, others will be in place to thwart an attack.
Reference: Cisco Tech Roles – CyberOps Engineer
What should a security analyst consider when comparing inline traffic interrogation with traffic tapping to determine which approach to use in the network?
- A . Tapping interrogation replicates signals to a separate port for analyzing traffic
- B . Tapping interrogations detect and block malicious traffic
- C . Inline interrogation enables viewing a copy of traffic to ensure traffic is in compliance with security policies
- D . Inline interrogation detects malicious traffic but does not block the traffic
A
Explanation:
Traffic tapping involves replicating network traffic and sending it to a separate port where it can be analyzed without affecting the original traffic flow. This allows security analysts to monitor and analyze traffic for potential threats without the risk of blocking legitimate traffic.
Reference: This explanation is based on general network security concepts, as the current page does not provide specific Cisco documentation.
