Practice Free 200-201 Exam Online Questions
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
- A . CSIRT
- B . PSIRT
- C . public affairs
- D . management
D
Explanation:
In the context of NIST’s incident response guidelines, management is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies. Management plays a key role in overseeing the incident response process to ensure that it is carried out effectively across all parts of the organization and that compliance with legal and regulatory requirements is maintained12.
Reference: = NIST SP 800-61 Rev. 2, Computer Security Incident Handling Guide1. InfraExam’s discussion on incident response stakeholder responsibilities
Which attack method intercepts traffic on a switched network?
- A . denial of service
- B . ARP cache poisoning
- C . DHCP snooping
- D . command and control
B
Explanation:
ARP cache poisoning is a type of attack that intercepts traffic on a switched network by sending spoofed ARP messages to associate the attacker’s MAC address with the IP address of a legitimate host or gateway. This way, the attacker can redirect the traffic intended for the legitimate host or gateway to his own device and perform a man-in-the-middle attack.
Reference: = Cisco Cybersecurity Operations Fundamentals
Which metric is used to capture the level of access needed to launch a successful attack?
- A . privileges required
- B . user interaction
- C . attack complexity
- D . attack vector
A
Explanation:
Privileges required is a metric in the Common Vulnerability Scoring System (CVSS) that measures the level of access needed to launch a successful attack. The higher the privileges required, the lower the severity of the vulnerability. The privileges required metric has three possible values: none, low, and high. None means that the attacker does not need any privileges to exploit the vulnerability. Low means that the attacker needs privileges that provide basic user capabilities. High means that the attacker needs privileges that provide significant or administrative control over the target.
Reference: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) – Cisco, page 2-17; 200-201 CBROPS – Cisco, exam topic 1.3.c
A security engineer notices confidential data being exfiltrated to a domain "Ranso4134-mware31-895" address that is attributed to a known advanced persistent threat group The engineer discovers that the activity is part of a real attack and not a network misconfiguration.
Which category does this event fall under as defined in the Cyber Kill Chain?
- A . reconnaissance
- B . delivery
- C . action on objectives
- D . weaponization
C
Explanation:
The event described falls under the ‘action on objectives’ category of the Cyber Kill Chain. This stage occurs after the attacker has established a foothold within the network and begins to execute their intended actions, such as data exfiltration.
Reference: The Cyber Kill Chain framework outlines the stages of a cyberattack, with ‘action on objectives’ being the final step where attackers achieve their primary goal, such as data theft
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received.
Which technology should the engineer use to accomplish this task?
- A . Firepower
- B . Email Security Appliance
- C . Web Security Appliance
- D . Stealthwatch
D
Explanation:
Stealthwatch is the technology that an engineer should use to fetch logs from a proxy server and generate actual events based on the data received. Cisco Secure Network Analytics, formerly known as Stealthwatch, provides the capability to configure proxy server logs so that the Flow Collector can receive the information. The Stealthwatch Management Console then displays this information on the Flow Proxy Records page, which includes URLs and application names of the traffic inside a network going through the proxy server1.
Reference: = Cisco Secure Network Analytics Proxy Log Configuration Guide
A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and writes to a new PHP file on the webserver.
Which event category is described?
- A . reconnaissance
- B . action on objectives
- C . installation
- D . exploitation
D
Explanation:
This event category is exploitation because the HTTP requests contain PHP code that attempts to execute commands on the web server and create a backdoor. Exploitation is the phase of the attack where the threat actor gains access to the target system and executes malicious code.
Reference: https://learningnetworkstore.cisco.com/on-demand-e-learning/understanding-cisco-cybersecurity-operations-fundamentals-cbrops-v1-0/CSCU-LP-CBROPS-V1-028093.html (Module 2, Lesson 2.1.3)
Which security principle is violated by running all processes as root or administrator?
- A . principle of least privilege
- B . role-based access control
- C . separation of duties
- D . trusted computing base
A
Explanation:
Running all processes as root or administrator violates the principle of least privilege, which states that users and processes should be granted only the minimum permissions necessary to perform their specific role or function within an organization. Running all processes as root or administrator gives them full access and control over the system, which increases the risk of unauthorized actions, malicious attacks, and accidental errors. It also makes it easier for attackers to escalate their privileges and compromise the system.
Reference: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) v1.0, Module 1: Security Concepts, Lesson 1.2: Security Principles
Cisco Certified CyberOps Associate Overview, Exam Topics, 1.1 Explain the CIA triad
Refer to the exhibit.
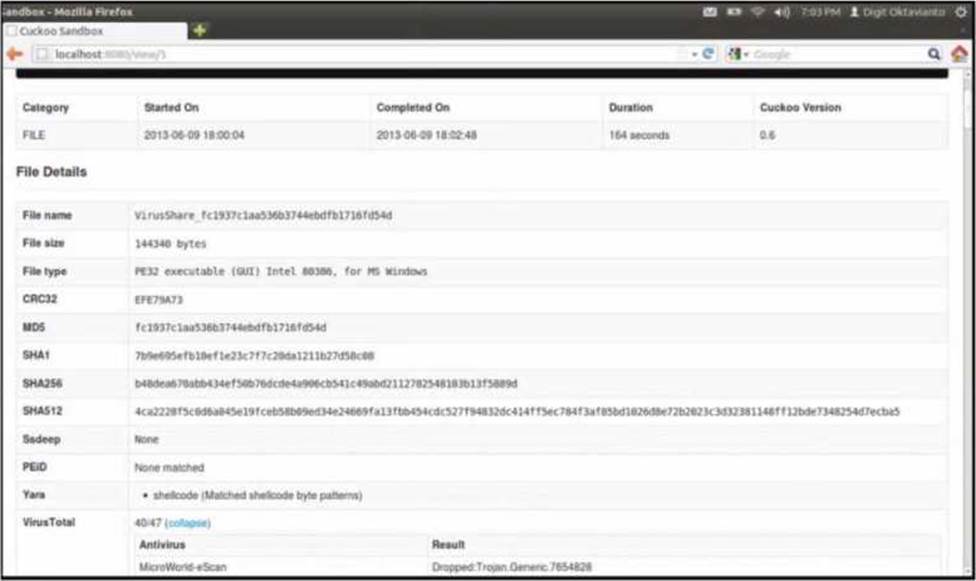
What does this Cuckoo sandbox report indicate?
- A . The file is spyware.
- B . The file will open unsecure ports when executed.
- C . The file will open a command interpreter when executed.
- D . The file is ransomware.
C
Explanation:
The Cuckoo sandbox report shows the analysis results of a file named "VirusShare_fc1937c1aa536b3744ebfb1716fd5f4d".
The file type is identified as a PE32 executable for MS Windows.
The "Yara" section indicates that the file contains shellcode, which matches specific shellcode byte patterns.
Shellcode typically indicates that the file will execute a payload, often used to open a command interpreter or execute commands directly.
Additionally, the antivirus result shows that the file was identified as containing a trojan (Trojan.Generic.7654828), which is consistent with behaviors such as opening a command interpreter for malicious purposes.
Reference: Cuckoo Sandbox Documentation
Analysis of Shellcode Behavior
Understanding Trojan Malware Functionality
What matches the regular expression c(rgr)+e?
- A . crgrrgre
- B . np+e
- C . c(rgr)e
- D . ce
A
Explanation:
The regular expression c(rgr)+e matches strings where “rgr” occurs one or more times between “c” and “e”. The string “crgrrgre” fits this pattern as it has the sequence “rgr” repeated twice between “c” and “e”. The plus sign (+) in the regular expression indicates that the preceding element must appear one or more times for a match to occur
What is a difference between SI EM and SOAR security systems?
- A . SOAR ingests numerous types of logs and event data infrastructure components and SIEM can fetch data from endpoint security software and external threat intelligence feeds
- B . SOAR collects and stores security data at a central point and then converts it into actionable intelligence, and SIEM enables SOC teams to automate and orchestrate manual tasks
- C . SIEM raises alerts in the event of detecting any suspicious activity, and SOAR automates investigation path workflows and reduces time spent on alerts
- D . SIEM combines data collecting, standardization, case management, and analytics for a defense-in-depth concept, and SOAR collects security data antivirus logs, firewall logs, and hashes of downloaded files
C
Explanation:
SIEM (Security Information and Event Management) systems are designed to collect, correlate, and analyze security event data from various sources to provide insights into potential security issues. They raise alerts when detecting suspicious activities. SOAR (Security Orchestration, Automation, and Response) systems, on the other hand, focus on automating and orchestrating incident response processes. They automate investigation path workflows and reduce the time spent on alerts by executing predefined actions and workflows in response to security events or incidents.
Reference: The differences between SIEM and SOAR are highlighted in various cybersecurity resources, including those provided by Palo Alto Networks and Exabeam, which explain that while SIEM primarily focuses on collecting and analyzing security event data, SOAR extends these capabilities through automation, orchestration, and predefined incident response playbooks
