Practice Free 200-201 Exam Online Questions
What specific type of analysis is assigning values to the scenario to see expected outcomes?
- A . deterministic
- B . exploratory
- C . probabilistic
- D . descriptive
A
Explanation:
This type of analysis is deterministic because it assigns fixed values to the scenario and calculates the expected outcomes based on those values. Deterministic analysis does not account for uncertainty or randomness in the scenario.
Reference: https://learningnetworkstore.cisco.com/on-demand-e-learning/understanding-cisco-cybersecurity-operations-fundamentals-cbrops-v1-0/CSCU-LP-CBROPS-V1-028093.html (Module 3, Lesson 3.1.2)
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network.
What is the impact of this traffic?
- A . ransomware communicating after infection
- B . users downloading copyrighted content
- C . data exfiltration
- D . user circumvention of the firewall
C
Explanation:
Traffic with a known TOR exit node is often associated with data exfiltration, where sensitive information is transferred from within the network to an external location. TOR networks are used to anonymize the traffic, making it difficult to trace back to the source.
Reference: = Cisco Cybersecurity Operations Fundamentals – Module 2: Security Monitoring
Which regex matches only on all lowercase letters?
- A . [a−z]+
- B . [^a−z]+
- C . a−z+
- D . a*z+
A
Explanation:
The regex [a−z]+ matches one or more lowercase letters from a to z. The plus sign (+) indicates that the preceding character set [a−z] can appear one or more times, thus matching strings of only lowercase letters1.
Reference: = This explanation is consistent with standard regex syntax as described in various programming and scripting languages documentation
What is the difference between a threat and a risk?
- A . Threat represents a potential danger that could take advantage of a weakness in a system
- B . Risk represents the known and identified loss or danger in the system
- C . Risk represents the nonintentional interaction with uncertainty in the system
- D . Threat represents a state of being exposed to an attack or a compromise, either physically or logically.
A
Explanation:
A threat represents a potential danger that could exploit a weakness in a system while risk is associated with the potential impact or loss that could occur if a threat exploits a vulnerability in the system. So, option A which states “Threat represents a potential danger that could take advantage of a weakness in a system” is correct.
Reference: = Cisco Certified CyberOps Associate Overview
A user received a targeted spear-phishing email and identified it as suspicious before opening the content.
To which category of the Cyber Kill Chain model does to this type of event belong?
- A . weaponization
- B . delivery
- C . exploitation
- D . reconnaissance
B
Explanation:
The delivery phase of the Cyber Kill Chain model involves the transmission of the weapon to the targeted environment. In the case of a spear-phishing email, the delivery is the act of sending the email to the user. The email itself is the weapon, designed to exploit the recipient’s trust to cause a breach
Refer to the exhibit.
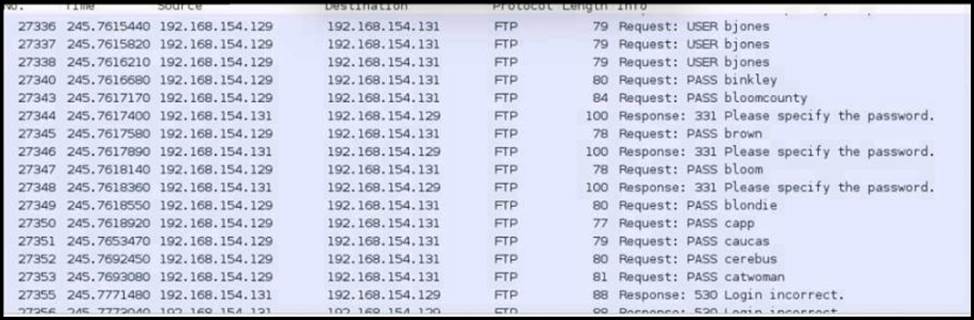
An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server.
Which display filters should the analyst use to filter the FTP traffic?
- A . dstport == FTP
- B . tcp.port==21
- C . tcpport = FTP
- D . dstport = 21
B
Explanation:
The correct display filter for analyzing FTP traffic in a PCAP file is “tcp.port==21”. This filter will show all TCP packets where the port number is 21, which is the standard port for FTP control messages.
What is the difference between deep packet inspection and stateful inspection?
- A . Stateful inspection verifies contents at Layer 4. and deep packet inspection verifies connection at Layer 7.
- B . Stateful inspection is more secure than deep packet inspection on Layer 7.
- C . Deep packet inspection is more secure than stateful inspection on Layer 4.
- D . Deep packet inspection allows visibility on Layer 7, and stateful inspection allows visibility on Layer 4.
C
Explanation:
Deep packet inspection (DPI) is a form of computer network packet filtering that examines the data part (and possibly also the header) of a packet as it passes an inspection point, searching for protocol non-compliance, viruses, spam, intrusions, or defined criteria to decide whether the packet may pass or if it needs to be routed to a different destination, or, for the purpose of collecting statistical information. It is a form of filtering employed at the security layer level of the OSI model. Stateful inspection, on the other hand, is a firewall technology that monitors the state of active connections and determines which network packets to allow through the firewall. Stateful inspection has largely replaced older technologies that were static and examined packets in isolation. Therefore, DPI is considered more secure because it examines the contents of the packets at Layer 7 (the application layer), while stateful inspection typically works up to Layer 4 (the transport layer).
Reference: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
An organization’s security team has detected network spikes coming from the internal network. An investigation has concluded that the spike in traffic was from intensive network scanning.
How should the analyst collect the traffic to isolate the suspicious host?
- A . by most active source IP
- B . by most used ports
- C . based on the protocols used
- D . based on the most used applications
A
Explanation:
To isolate the suspicious host that is performing intensive network scanning, the analyst should collect the traffic by most active source IP. This will help to identify the IP address of the host that is generating the most traffic and sending the most packets or bytes. The analyst can then apply filters or queries to analyze the traffic from that source IP and determine the nature and scope of the scanning activity.
Reference: = Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) – Cisco, page 72; [Cisco CyberOps Associate CBROPS 200-201 Official Cert Guide], page 468
What is the communication channel established from a compromised machine back to the attacker?
- A . man-in-the-middle
- B . IDS evasion
- C . command and control
- D . port scanning
C
Explanation:
The communication channel established from a compromised machine back to the attacker is known as a command and control (C2) channel. This channel allows attackers to maintain communication with the compromised system, issue commands, and potentially exfiltrate data. The C2 channel can be established using various protocols and methods to evade detection and maintain persistence.
Which tool gives the ability to see session data in real time?
- A . tcpdstat
- B . trafdump
- C . tcptrace
- D . trafshow
D
Explanation:
: Trafshow is a network monitoring tool that provides real-time monitoring of network traffic. It displays the current connections and the amount of data being transferred over those connections. It is particularly useful in a Security Operations Center (SOC) for identifying unusual traffic patterns or connections that may indicate a security incident.
Reference: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
