Practice Free 200-201 Exam Online Questions
Which attack method is being used when an attacker tries to compromise a network with an authentication system that uses only 4-digit numeric passwords and no username?
- A . SQL injection
- B . dictionary
- C . replay
- D . cross-site scripting
B
Explanation:
A dictionary attack is a method used to break into a password-protected computer or server by systematically entering every word in a dictionary as a password. In the context of an authentication system that uses only 4-digit numeric passwords, a dictionary attack would involve trying all possible combinations of 4-digit numbers until the correct one is found.
Reference: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) course materials discuss various attack methods, including dictionary attacks, and how they can be used to compromise networks
When an event is investigated, which type of data provides the investigate capability to determine if data exfiltration has occurred?
- A . full packet capture
- B . NetFlow data
- C . session data
- D . firewall logs
A
Explanation:
Full packet capture provides the complete recording of all the packets that are transmitted over the network. This data is essential for in-depth analysis during an investigation, as it allows investigators to reconstruct the session, observe the content of the traffic, and determine if data exfiltration has occurred.
Reference: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) study materials
would typically cover the importance of full packet capture in network forensics and incident response.
Refer to the exhibit.
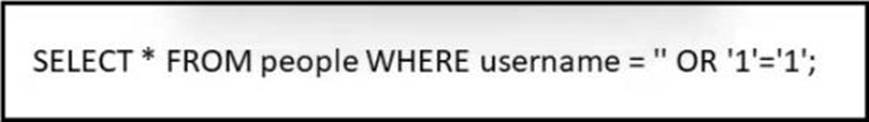
Which type of attack is being executed?
- A . SQL injection
- B . cross-site scripting
- C . cross-site request forgery
- D . command injection
A
Explanation:
The exhibit shows a SQL query that is attempting to bypass login controls by modifying the query to always return true. This is a common tactic used in SQL injection attacks where malicious SQL statements are inserted into an entry field for execution.
Reference: = Cisco Cybersecurity Source Documents
Reference: https://www.w3schools.com/sql/sql_injection.asp
During which phase of the forensic process are tools and techniques used to extract information from the collected data?
- A . investigation
- B . examination
- C . reporting
- D . collection
B
Explanation:
During the examination phase of the forensic process, digital forensic investigators use various tools and techniques to extract and analyze information from the collected data. This phase involves detailed scrutiny of the data to uncover relevant evidence and is critical for the success of the forensic investigation.
Reference: The explanation aligns with the standard phases of digital forensics, which include identification, preservation, examination, documentation, and presentation as outlined in digital forensics literature and guidelines.
How is NetFlow different from traffic mirroring?
- A . NetFlow collects metadata and traffic mirroring clones data.
- B . Traffic mirroring impacts switch performance and NetFlow does not.
- C . Traffic mirroring costs less to operate than NetFlow.
- D . NetFlow generates more data than traffic mirroring.
A
Explanation:
NetFlow is a network protocol developed by Cisco for collecting IP traffic information and monitoring network traffic. It collects metadata of the IP traffic flowing across networking devices like routers and switches. On the other hand, Traffic mirroring involves capturing all the data packets that flow through a particular point in the network to analyze or inspect them later.
Reference: = Cisco Cybersecurity Operations Fundamentals
A threat actor penetrated an organization’s network.
Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
- A . event name, log source, time, source IP, and host name
- B . protocol, source IP, source port, destination IP, and destination port
- C . event name, log source, time, source IP, and username
- D . protocol, log source, source IP, destination IP, and host name
B
Explanation:
The 5-tuple approach consists of protocol, source IP address, source port number, destination IP address, and destination port number to uniquely identify sessions between endpoints on a network.
Reference: = Cisco Cybersecurity Source Documents
Reference: https://blogs.cisco.com/security/the-dreaded-5-tuple
Refer to the exhibit.
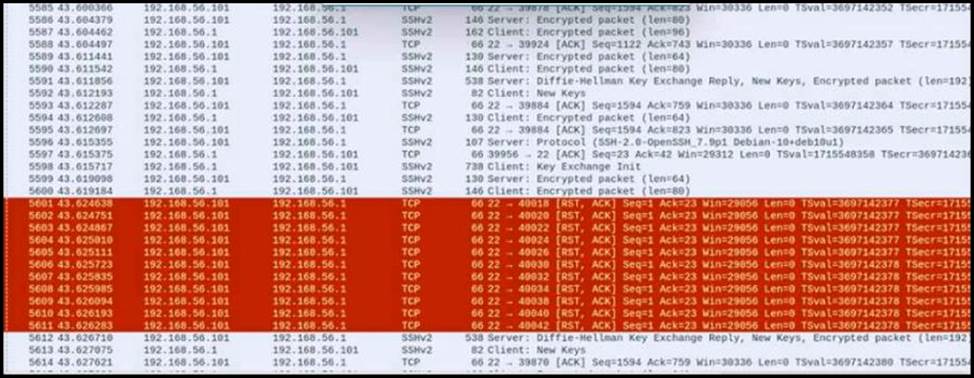
An engineer is analyzing a PCAP file after a recent breach An engineer identified that the attacker used an aggressive ARP scan to scan the hosts and found web and SSH servers. Further analysis showed several SSH Server Banner and Key Exchange Initiations. The engineer cannot see the exact data being transmitted over an encrypted channel and cannot identify how the attacker gained access.
How did the attacker gain access?
- A . by using the buffer overflow in the URL catcher feature for SSH
- B . by using an SSH Tectia Server vulnerability to enable host-based authentication
- C . by using an SSH vulnerability to silently redirect connections to the local host
- D . by using brute force on the SSH service to gain access
D
Explanation:
The scenario described involves an attacker conducting an aggressive ARP scan followed by multiple SSH Server Banner and Key Exchange Initiations. The lack of visibility into the encrypted data transmitted over the SSH channel suggests that the attacker may have gained access by brute-forcing the SSH service. This method involves attempting numerous combinations of usernames and passwords until the correct credentials are found, allowing unauthorized access to the server.
Reference: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) course1.
Cisco Cybersecurity documents and resources
An engineer configured regular expression “.”.(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1 .[01]" on Cisco ASA firewall.
What does this regular expression do?
- A . It captures documents in an HTTP network session.
- B . It captures .doc, .xls, and .pdf files in HTTP v1.0 and v1.1.
- C . It captures .doc, .xls, and .ppt files extensions in HTTP v1.0.
- D . It captures Word, Excel, and PowerPoint files in HTTPv1.0 and v1.1.
D
Explanation:
The regular expression provided is: ..(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1 .[01] This regular expression is designed to match file extensions for Word (.doc), Excel (.xls), and PowerPoint (.ppt) files in HTTP network sessions.
The regular expression uses character classes and alternatives to match different case variations of these file extensions.
The part ..(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) matches the file extensions, and HTTP/1 .[01] ensures that the match is in the context of HTTP version 1.0 or 1.1.
Reference: Cisco ASA Regular Expressions Documentation
Understanding Regular Expressions in Network Security
Filtering and Capturing HTTP Traffic with Regex
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
- A . queries Linux devices that have Microsoft Services for Linux installed
- B . deploys Windows Operating Systems in an automated fashion
- C . is an efficient tool for working with Active Directory
- D . has a Common Information Model, which describes installed hardware and software
D
Explanation:
Windows Management Instrumentation (WMI) provides a unified way for users to request system information, including hardware and software inventory data. The Common Information Model (CIM) is an open standard that defines how managed elements in an IT environment are represented as a common set of objects and relationships between them.
Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/2-4/admin_guide/b_ise_admin_guide_24/b_ise_admin_guide_24_new_chapter_01100.html
What is the difference between indicator of attack (loA) and indicators of compromise (loC)?
- A . loA is the evidence that a security breach has occurred, and loC allows organizations to act before the vulnerability can be exploited.
- B . loA refers to the individual responsible for the security breach, and loC refers to the resulting loss.
- C . loC is the evidence that a security breach has occurred, and loA allows organizations to act before the vulnerability can be exploited.
- D . loC refers to the individual responsible for the security breach, and loA refers to the resulting loss.
C
Explanation:
Indicators of Compromise (IoC) are pieces of forensic data, such as system log entries or files, that suggest an intrusion may have occurred. Indicators of Attack (IoA) are signs that an attack may be underway, allowing organizations to take action before any potential breach occurs.
Reference: The CBROPS course materials cover the concepts of IoC and IoA, explaining how they are used in cybersecurity operations to detect and prevent security incidents.
