Practice Free H12-891_V1.0-ENU Exam Online Questions
Which of the following reasons may cause IS-IS neighbor relationship failure? (Multiple choice)
- A . The IS-IS Levels at both ends of the link do not match.
- B . When establishing an IS-IS Level-1 neighbor, the area numbers of the devices at both ends of the link do not match.
- C . The devices at both ends of the link are configured with the same System ID.
- D . The IP addresses of the interfaces at both ends of the link are not in the same network segment.
Regarding the description of Network Address Port Translation (NAPT) and Network Address Only Translation (No-PAT), which of the following statements is correct?
- A . After NAPT conversion, for external network users, all packets will only come from the same IP address.
- B . No-PAT supports protocol address translation at the network layer
- C . NAPT only supports protocol address translation at the network layer
- D . No-PAT only supports protocol port conversion at the transport layer
Four routers run IS-IS and have established adjacencies. The area numbers and router levels are marked in the figure. If route penetration is configured on the R3 device, what is the Cost value for R4 to reach 10.0.2.2/32?
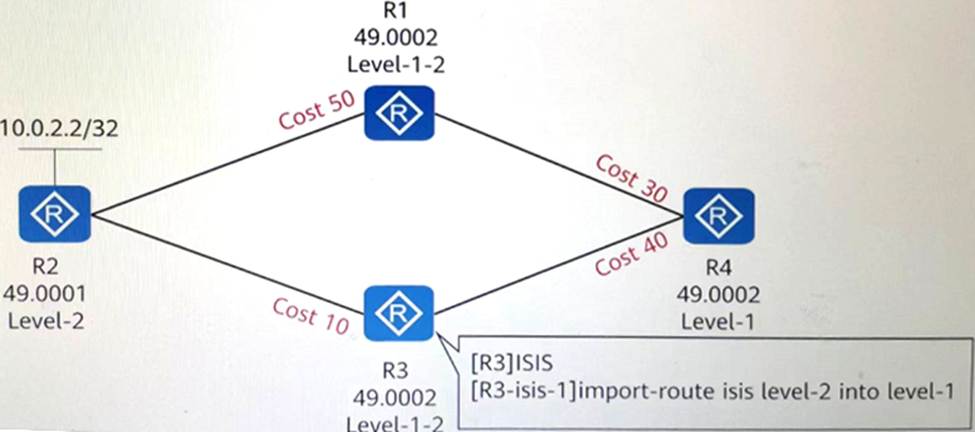
- A . 80
- B . 50
- C . 30
- D . 40
As shown in the figure, in the scenario of dynamically establishing a VXLAN tunnel through BGP EVPN, which of the following RT values is carried by the BGP EVPN Type2 route sent by VTEP1 to VTEP2?
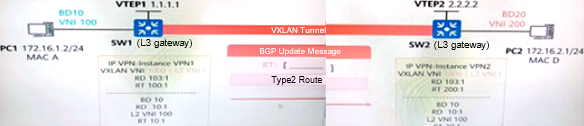
- A . 10:1
- B . 200:1
- C . 20:1
- D . 100:1
When the BitString length is 256 bits, there can only be a maximum of 256 BFRs in the BIER field.
- A . True
- B . False
Which LSAs in OSPFv3 can be flooded within an area? (Multiple choice)
- A . Inter-Area-Prefix-LSA
- B . Inter-Area-Router-LSA
- C . Link-LSA
- D . Intra-Area-Prefix-LSA
802.1X authentication is deployed in the network as shown in the figure. By default, which of the following packets cannot trigger 802.1X authentication?
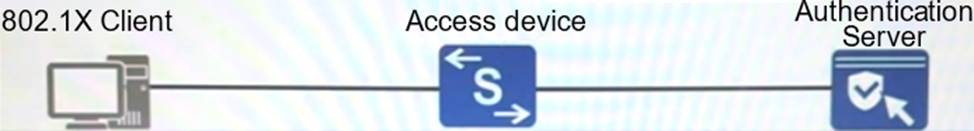
- A . DHCP
- B . ND
- C . EAPoL
- D . ICMP
According to different bearer technologies, the bearer modes of traditional wide-area bearer networks can be divided into MPLS bearer modes and () bearer modes.
It is known that the SSH client uses username and password authentication. During the user authentication phase, the SSH client sends an SSH_MSG_USERAUTH_REQUEST message. This message does not contain which of the following fields?
- A . Session ID
- B . Username
- C . Authentication method
- D . Password
Which of the following descriptions about access control in small and medium-sized campuses is wrong?
- A . iMaster NCE supports connecting to third-party RADIUS servers
- B . iMaster NCE supports directly serving as an authentication server
- C . Cloud AP supports Portal local authentication
- D . iMaster NCE supports serving as a Portal relay device
