Practice Free NSE7_OTS-7.2 Exam Online Questions
Which three Fortinet products can you use for device identification in an OT industrial control system (ICS)? (Choose three.)
- A . FortiSIEM
- B . FortiManager
- C . FortiAnalyzer
- D . FortiGate
- E . FortiNAC
How can you achieve remote access and internet availability in an OT network?
- A . Create a back-end backup network as a redundancy measure.
- B . Implement SD-WAN to manage traffic on each ISP link.
- C . Add additional internal firewalls to access OT devices.
- D . Create more access policies to prevent unauthorized access.
You are investigating a series of incidents that occurred in the OT network over past 24 hours in FortiSIEM.
Which three FortiSIEM options can you use to investigate these incidents? (Choose three.)
- A . Security
- B . IPS
- C . List
- D . Risk
- E . Overview
Refer to the exhibit, which shows a non-protected OT environment.
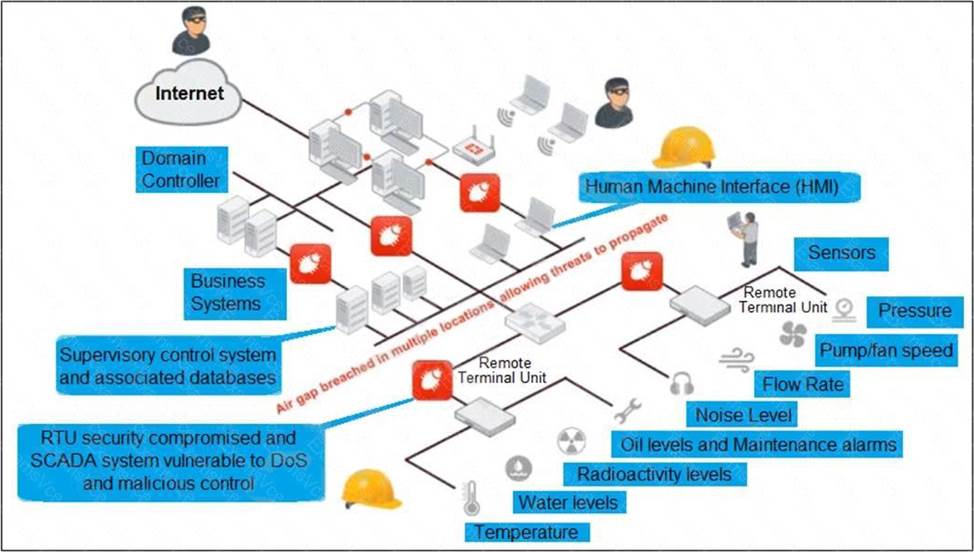
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
- A . Deploy an edge FortiGate between the internet and an OT network as a one-arm sniffer.
- B . Deploy a FortiGate device within each ICS network.
- C . Configure firewall policies with web filter to protect the different ICS networks.
- D . Configure firewall policies with industrial protocol sensors
- E . Use segmentation
What can be assigned using network access control policies?
- A . Layer 3 polling intervals
- B . FortiNAC device polling methods
- C . Logical networks
- D . Profiling rules
Refer to the exhibit.
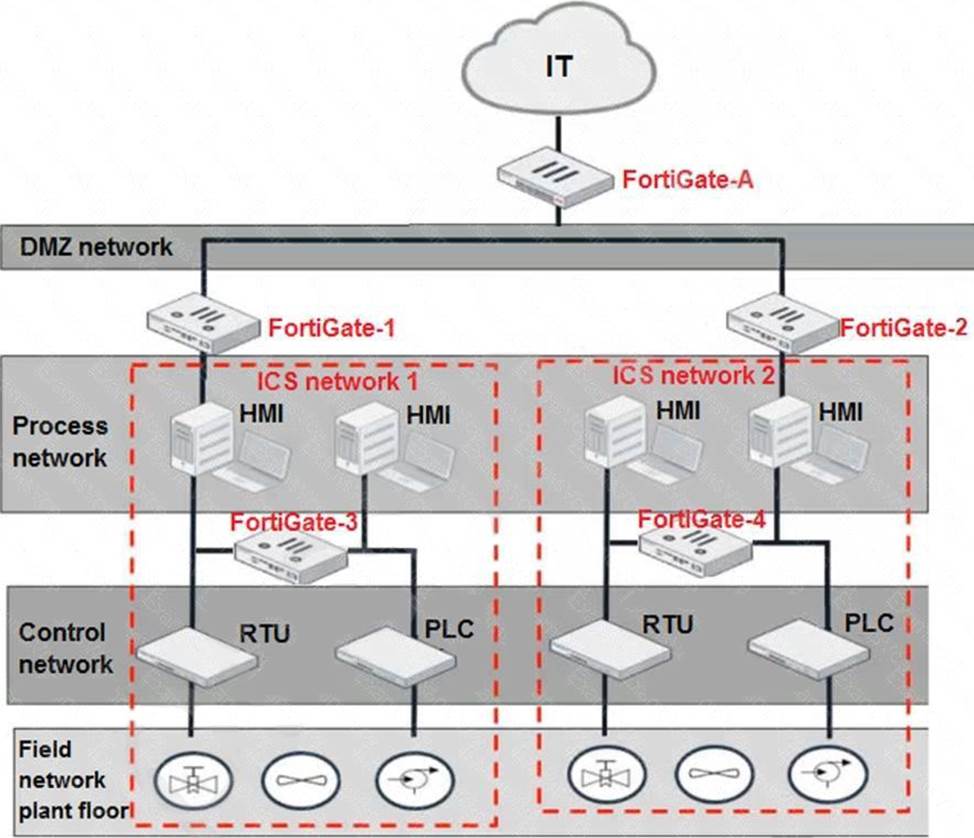
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
- A . Firewall policies should be configured on FortiGate-3 and FortiGate-4 with industrial protocol sensors.
- B . Micro-segmentation can be achieved only by replacing FortiGate-3 and FortiGate-4 with a pair of FortiSwitch devices.
- C . IT and OT networks are separated by segmentation.
- D . FortiGate-3 and FortiGate-4 devices must be in a transparent mode.
Refer to the exhibits.
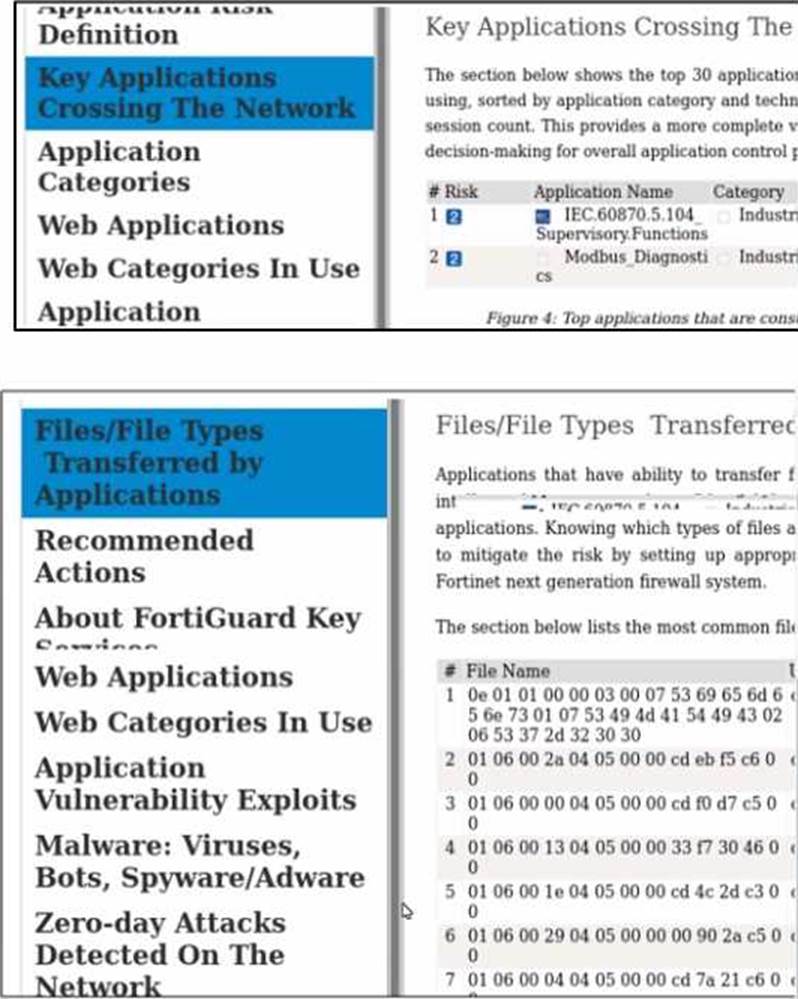
Which statement about some of the generated report elements from FortiAnalyzer is true?
- A . The report confirms Modbus and IEC 104 are the key applications crossing the network.
- B . FortiGate collects the logs and generates the report to FortiAnalyzer.
- C . The file types confirm the infected applications on the PLCs.
- D . This report is predefined and is not available for customization.
Which statemenl about the IEC 104 protocol is true?
- A . IEC 104 is used for telecontrol SCADA in electrical engineering applications.
- B . IEC 104 is IEC 101 compliant in old SCADA systems.
- C . IEC 104 protects data transmission between OT devices and services.
- D . IEC 104 uses non-TCP/IP standards.
An OT administrator configured and ran a default application risk and control report in FortiAnalyzer to learn more about the key application crossing the network. However, the report output is empty despite the fact that some related real-time and historical logs are visible in the FortiAnalyzer.
What are two possible reasons why the report output was empty? (Choose two.)
- A . The administrator selected the wrong logs to be indexed in FortiAnalyzer.
- B . The administrator selected the wrong time period for the report.
- C . The administrator selected the wrong devices in the Devices section.
- D . The administrator selected the wrong hcache table for the report.
B, C
Explanation:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/32cb817d-a307-11eb-b70b-00505692583a/FortiAnalyzer-7.0.0-Administration_Guide.pdf
Which type of attack posed by skilled and malicious users of security level 4 (SL 4) of IEC 62443 is designed to defend against intentional attacks?
- A . Users with access to moderate resources
- B . Users with low access to resources
- C . Users with unintentional operator error
- D . Users with substantial resources
