Practice Free D-ISM-FN-23 Exam Online Questions
In a bridged iSCSI network, which type of network enables the iSCSI gateway to connect servers to storage systems?
- A . Server N_Ports ports and storage system Ethernet Ports
- B . Server EX_Ports ports and storage system Ethernet Ports
- C . Server Ethernet ports and storage system N_Ports
- D . Server Ethernet ports and storage system EX_Ports
What describes an incident in a storage infrastructure?
- A . Unknown root cause of one or more disruptions to service
- B . Support request to help access an IT resource
- C . Any action that may impact the functionality of the system
- D . Any event that prevents ions of known errors
Which exhibit represents a Type 2 hypervisor?
A)
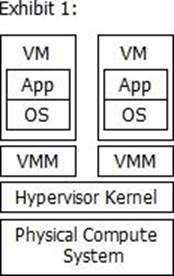
B)
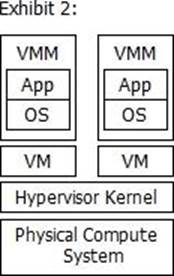
C)
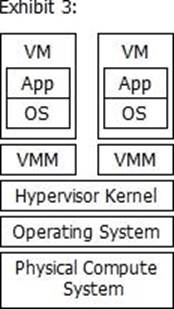
D)
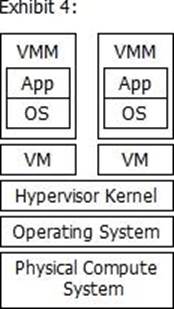
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Which factor has contributed to the growth of digital data?
- A . Proliferation of applications and smart devices
- B . Consolidation of infrastructure elements
- C . Deduplication of the existing data
- D . Adoption of storage virtualization technologies
Why is it important for organizations to store, protect, and manage their data?
- A . Reduce the amount of data to be replicated, migrated, and backed up.
- B . Rapidly develop and deploy modern applications for business improvement.
- C . Develop new business opportunities by leveraging existing data.
- D . Reduce the complexity in managing the data center environment.
An organization is evaluating a cloud deployment solution that allows them to select various cloud service providers. They want to avoid vendor lock-in issues while optimizing performance and cost.
Which recommended cloud deployment model will meet their requirements?
- A . Private cloud
- B . Community cloud
- C . Public cloud
- D . Multi-cloud
Which EMC product provides a software-defined storage platform to create a compute-based storage area network?
- A . ScaleIO
- B . XtremIO
- C . Isilon
- D . Atmos
An organization performs a full back up every Sunday and cumulative back ups on the remaining days. On Thursday, a data corruption occurs that requires a data restoration from the backup copies.
How many backup copies are required to perform this restoration?
- A . 1
- B . 2
- C . 3
- D . 4
What is an accurate statement about Zoning?
- A . FC switch ports, FC HBA ports, and storage ports should not be members of multiple zones
- B . Nodes that are distributed across multiple switches in a switched fabric may also be grouped into the same zone
- C . Increases the amount of fabric-management traffic within a zone by sending RSCNs to all nodes in a fabric
- D . Multiple zone sets may be defined in a fabric and all zone sets must be active at a time
What is a goal of cyber recovery?
- A . Isolate copies of critical data to ensure that an uncompromised copy always exists
- B . Abstract the physical compute hardware from the operating system and applications
- C . Evaluate systems, networks, and applications to find vulnerabilities
- D . Determine persistence access of system, networks, and applications
