Practice Free NSE6_FNC-7.2 Exam Online Questions
Where are logical network values defined?
- A . In the model configuration view of each infrastructure device
- B . In the port properties view of each port
- C . On the profiled devices view
- D . In the security and access field of each host record
An administrator wants the Host At Risk event to generate an alarm.
What is used to achieve this result?
- A . A security trigger activity
- B . A security filter
- C . An event to alarm mapping
- D . An event to action mapping
Refer to the exhibit.
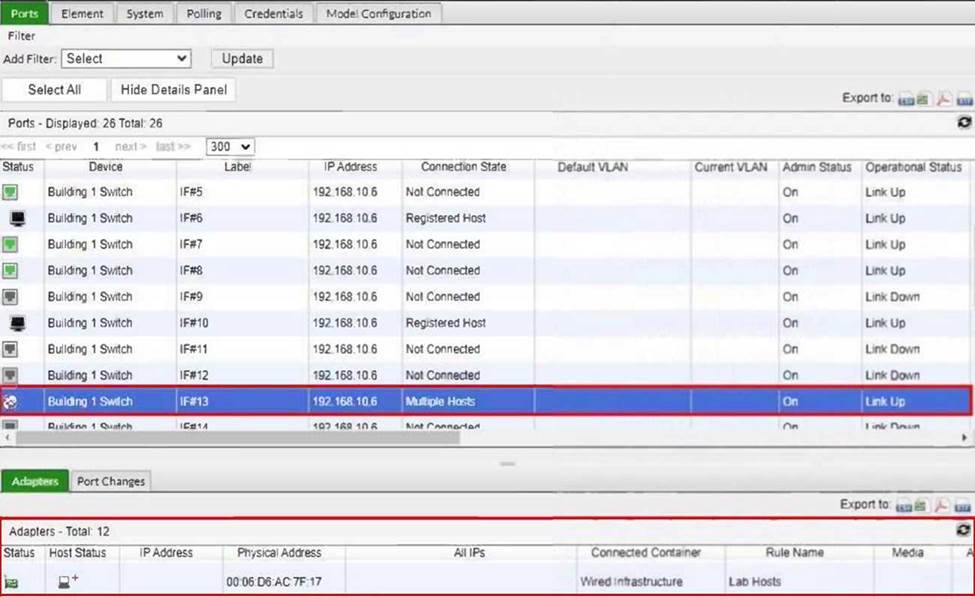
What would happen if the highlighted port with connected hosts was placed in both the Forced Registration and Forced Remediation port groups?
- A . Multiple enforcement groups could not contain the same port.
- B . Only the higher ranked enforcement group would be applied.
- C . Both types of enforcement would be applied.
- D . Enforcement would be applied only to rogue hosts.
Where do you look to determine which network access policy, if any is being applied to a particular host?
- A . The Policy Details view for the host
- B . The Connections view
- C . The Port Properties view of the hosts port
- D . The Policy Logs view
What agent is required in order to detect an added USB drive?
- A . Persistent
- B . Dissolvable
- C . Mobile
- D . Passive
Refer to the exhibit.
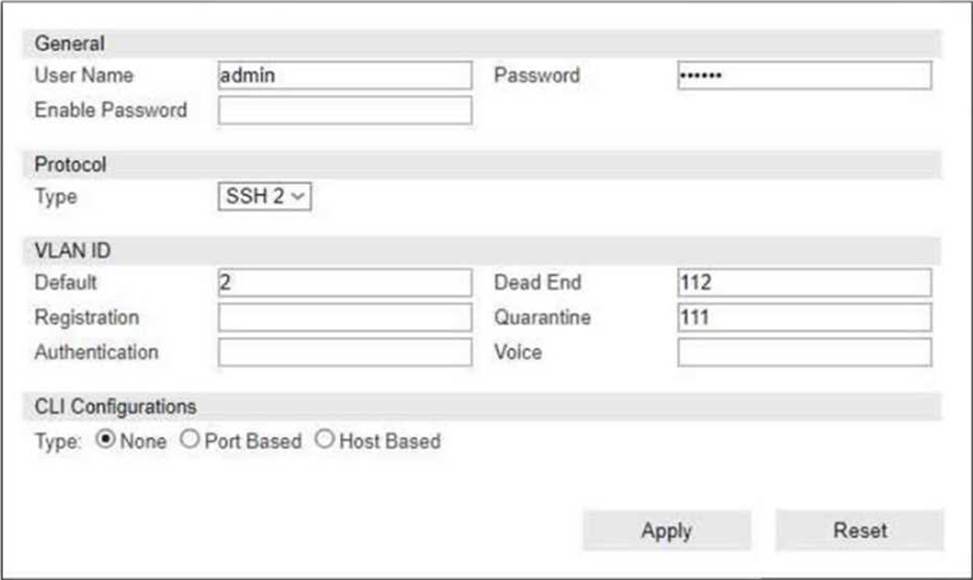
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what occurs?
- A . The host is moved to VLAN 111.
- B . The host is moved to a default isolation VLAN.
- C . No VLAN change is performed.
- D . The host is disabled.
When FortiNAC is managing FortiGate VPN users, why is an endpoint compliance policy necessary?
- A . To confirm installed security software
- B . To validate the VPN user credentials
- C . To designate the required agent type
- D . To validate the VPN client being used
By default, if more than 20 hosts are seen connected on a single port simultaneously, what will happen to the port?
- A . The port is switched into the Dead-End VLAN.
- B . The port becomes a threshold uplink.
- C . The port is disabled.
- D . The port is added to the Forced Registration group.
In an isolation VLAN which three services does FortiNAC supply? (Choose three.)
- A . NTP
- B . DHCP
- C . Web
- D . DNS
- E . ISMTP
Refer to the exhibit, and then answer the question below.

Which host is rogue?
- A . 1
- B . 3
- C . 2
- D . 4
